SOC141 - Phishing URL Detected
EventID : 86 Event Time : Mar, 22, 2021, 09:23 PM Rule : SOC141 - Phishing URL Detected Level : Security Analyst
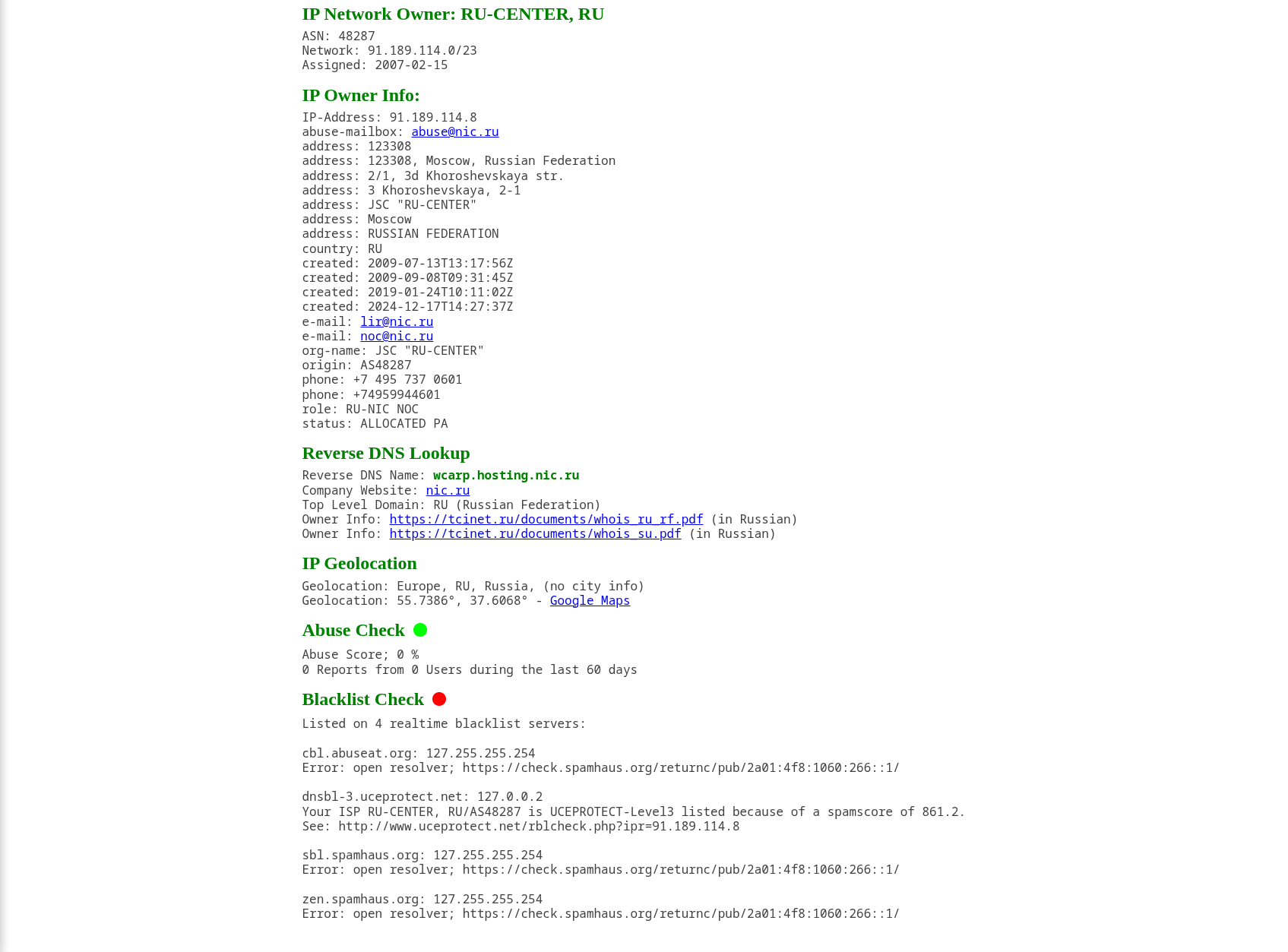
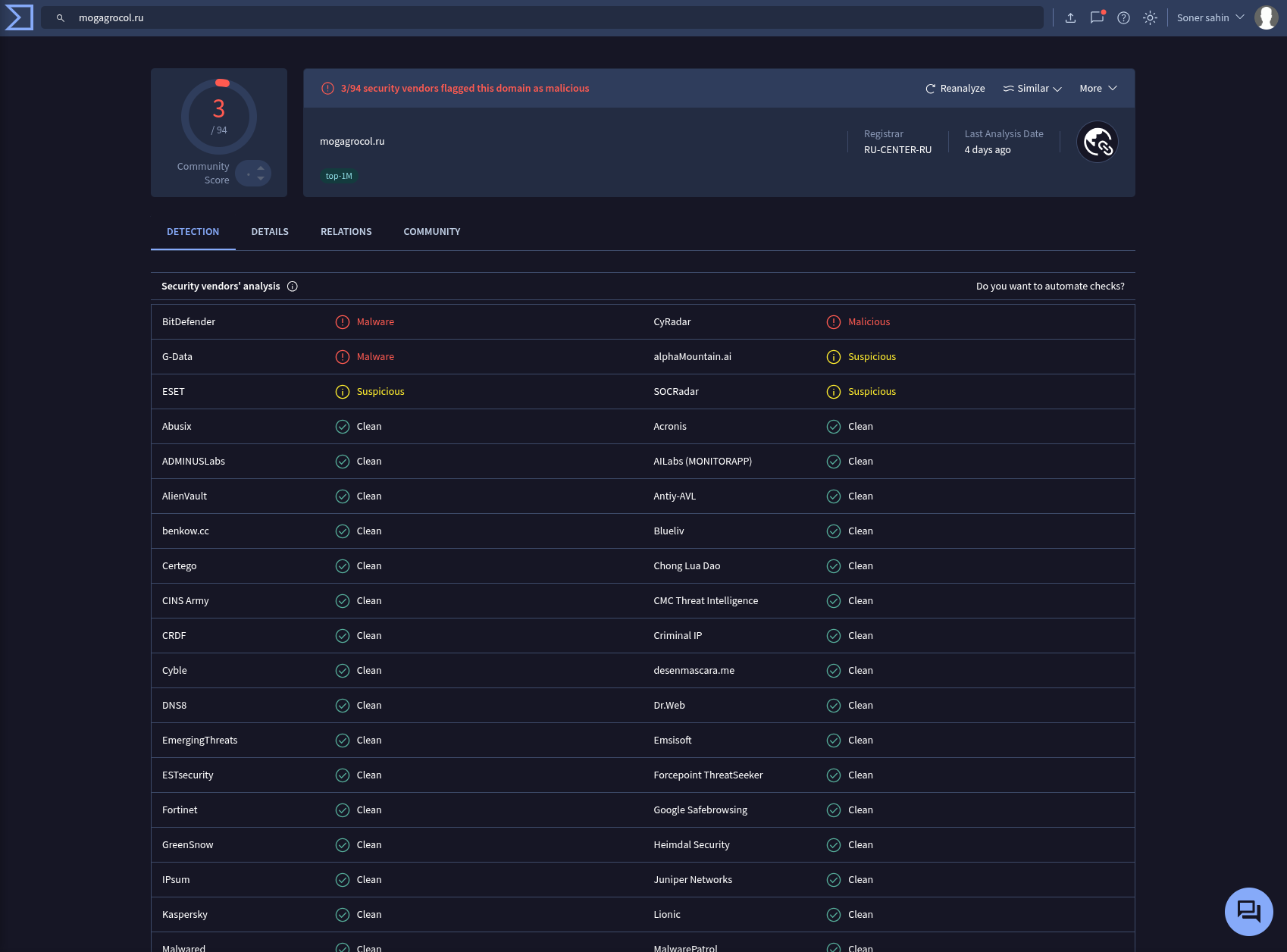
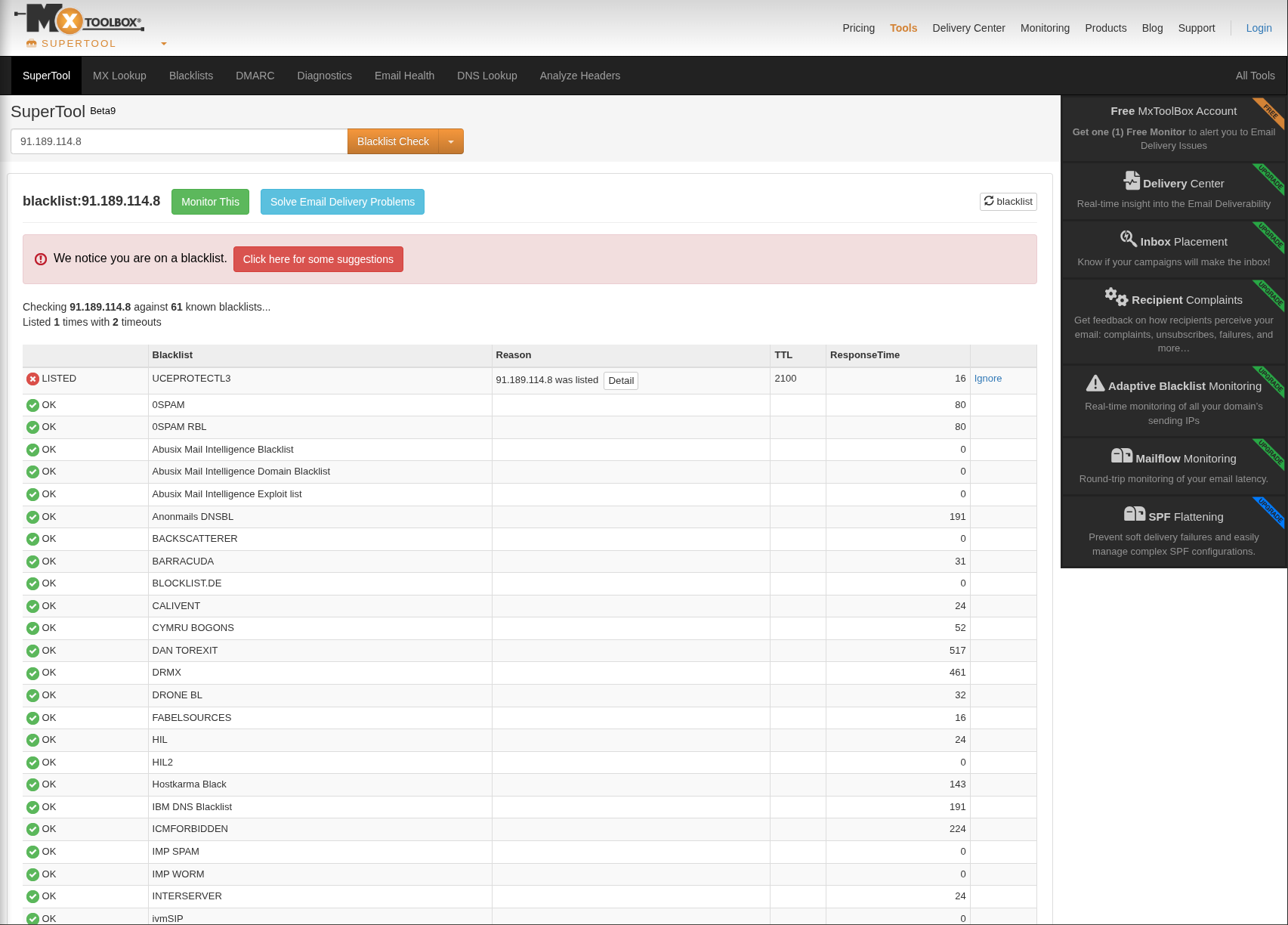
Source Address : 172.16.17.49 Source Hostname : EmilyComp Destination Address : 91.189.114.8 Destination Hostname : mogagrocol.ru
Username : ellie Request URL : http://mogagrocol.ru/wp-content/plugins/akismet/fv/index.php?email=ellie@letsdefend.io User Agent : Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.88 Safari/537.36
Device Action : Allowed
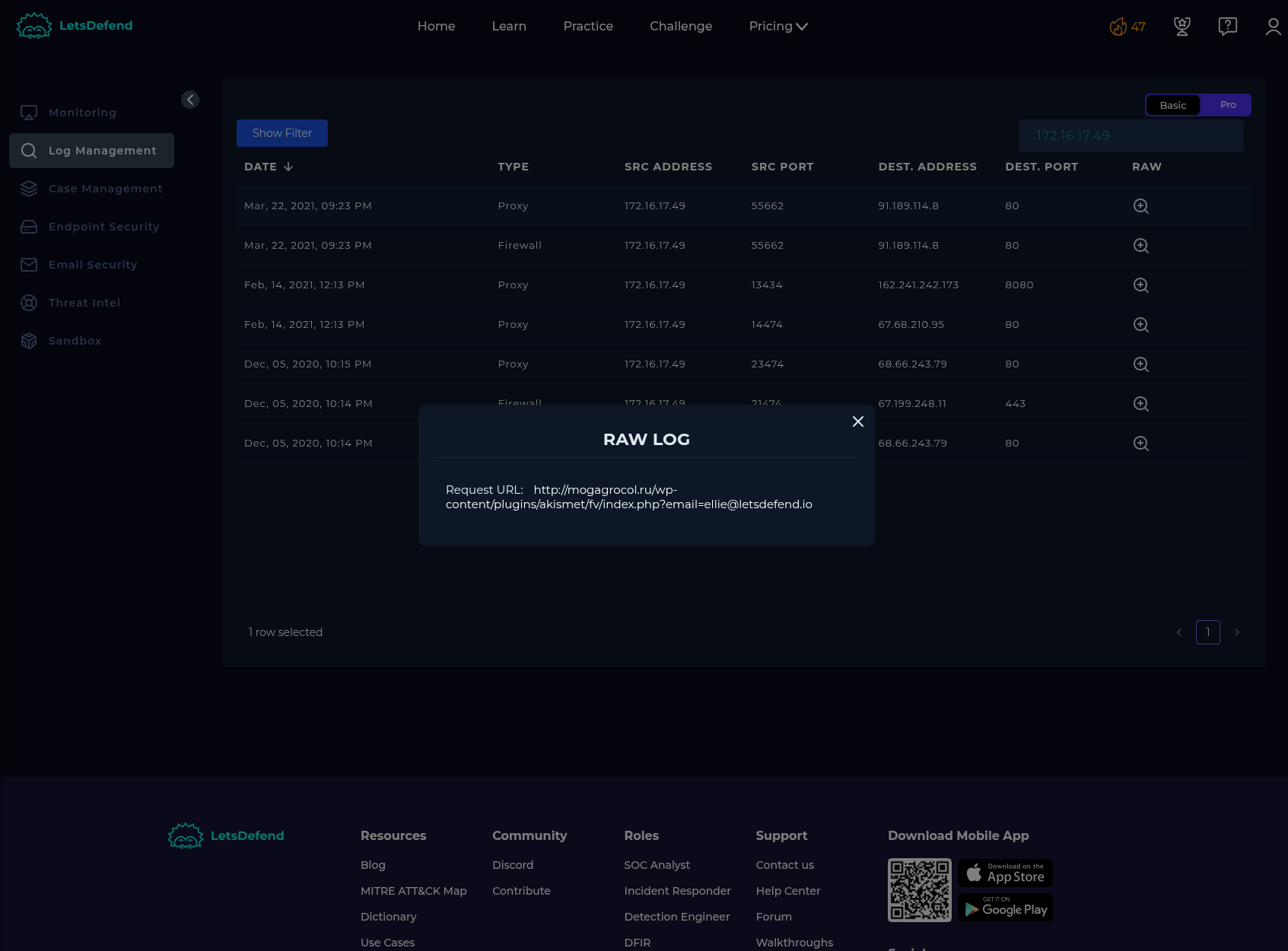
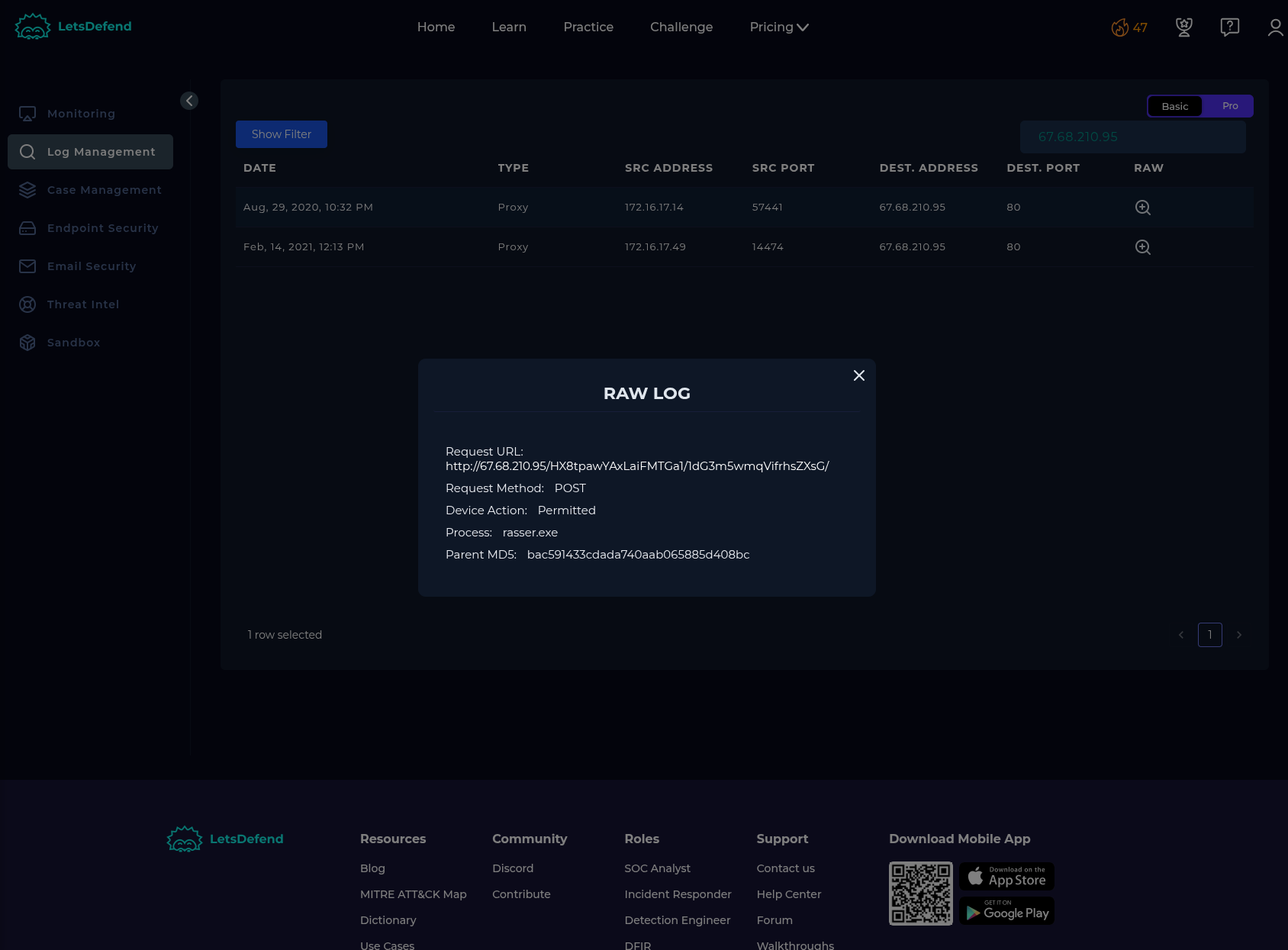
Log Management:
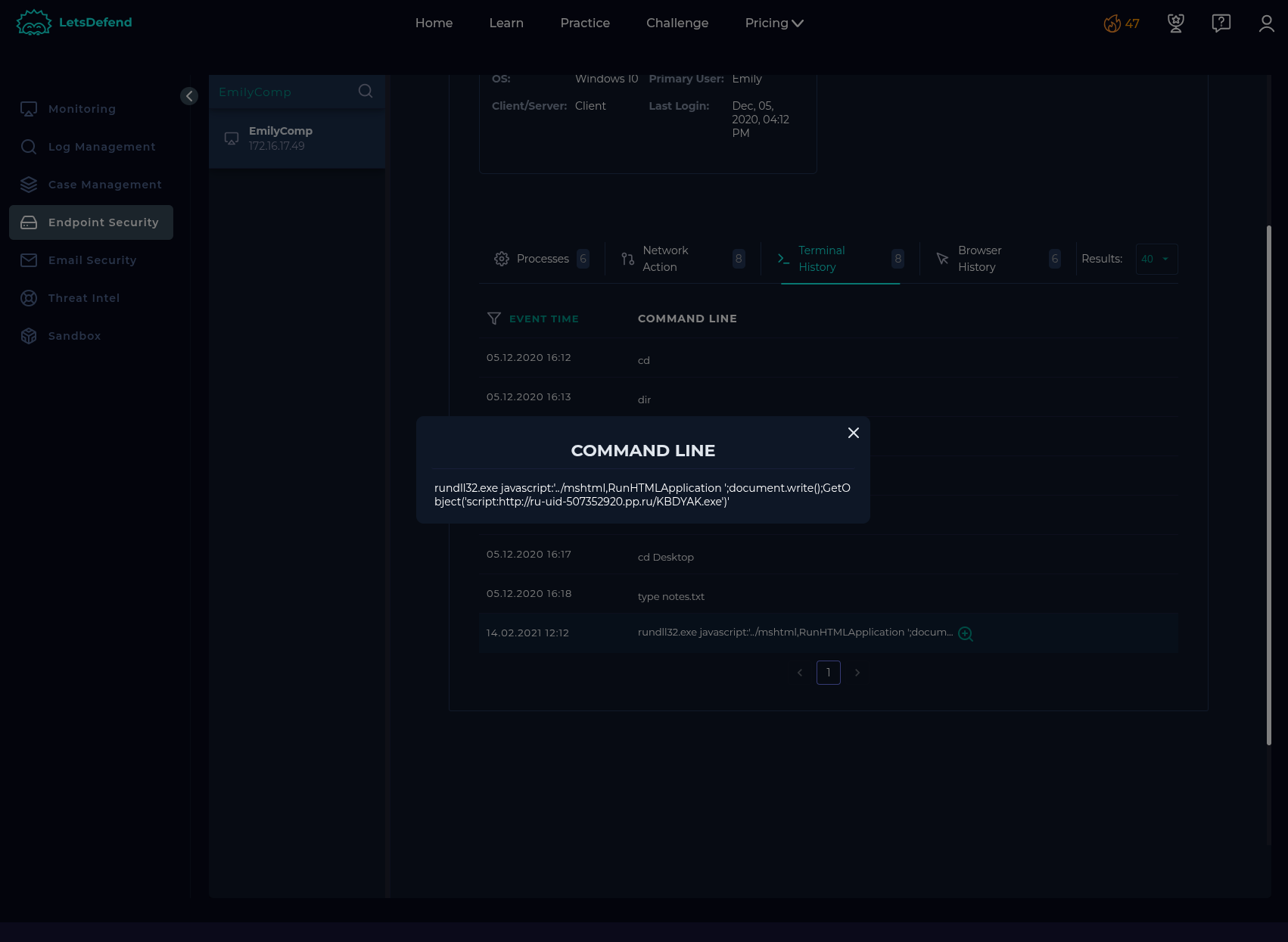
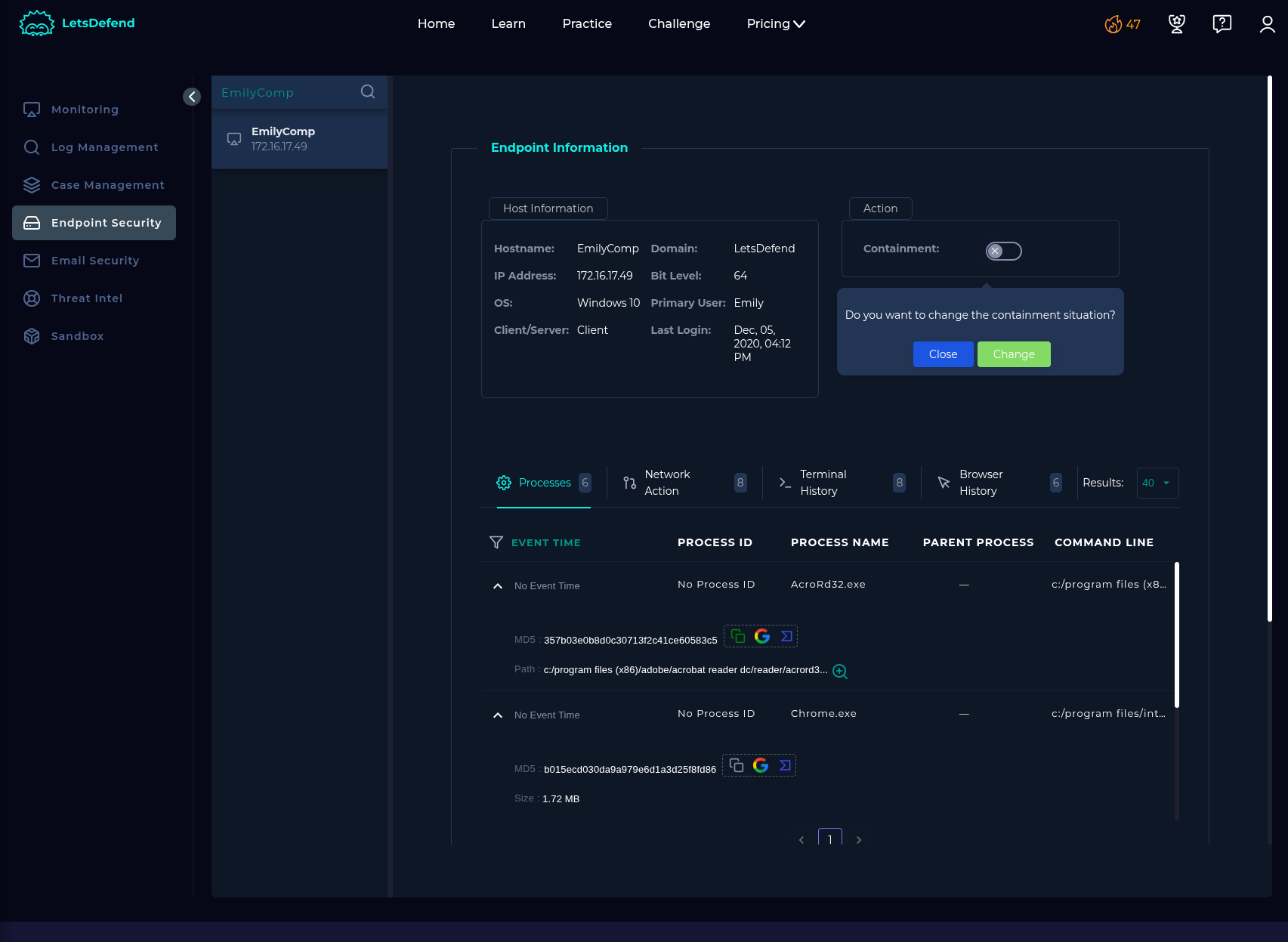
Endpoint Security:

Threat Intelligence:
Analyst Note:
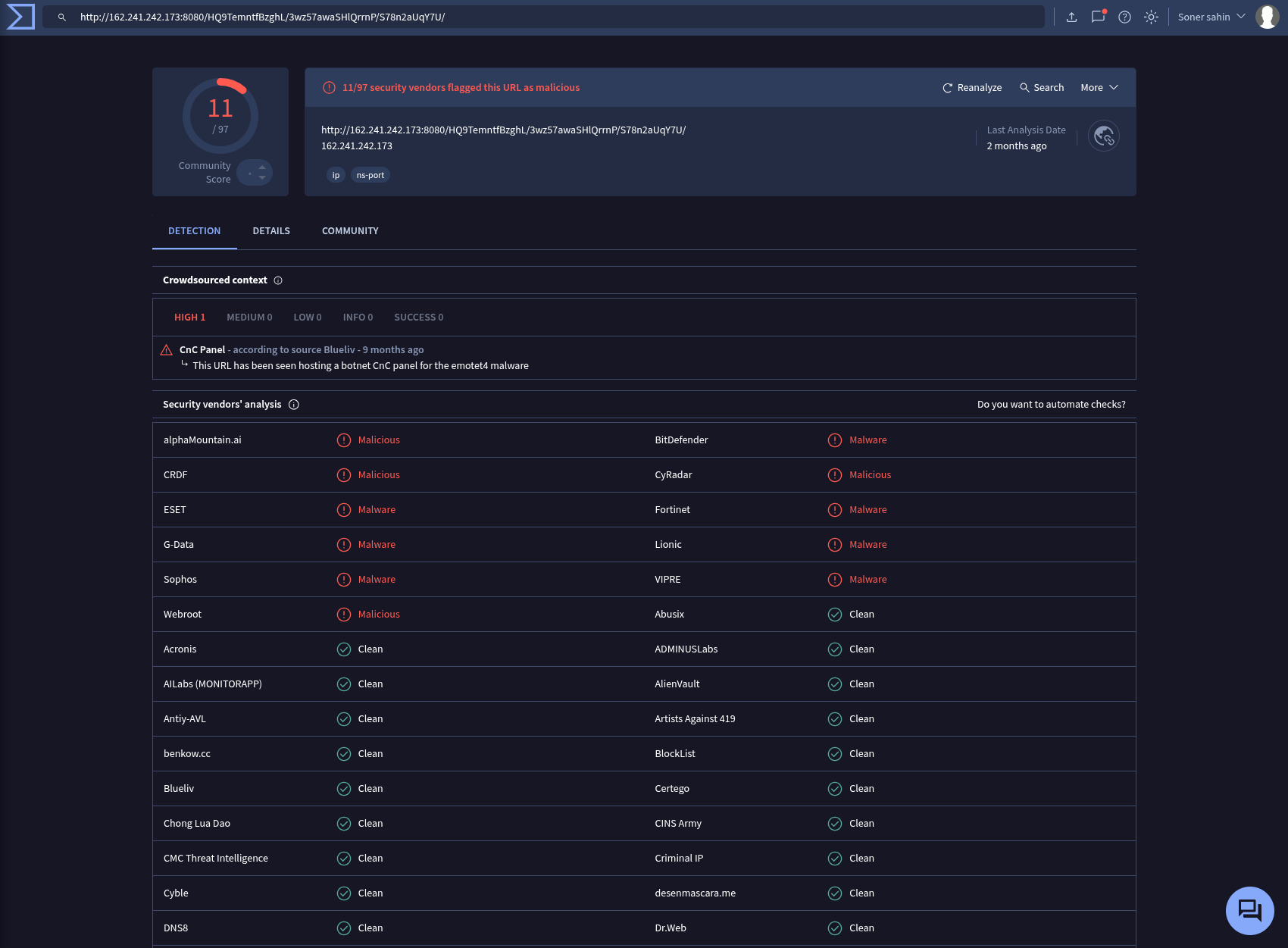
According to my investigation, I noticed that EmilComp named machine requested an malicious URL (http://mogagrocol.ru/wp-content/plugins/akismet/fv/index.php?email=ellie@letsdefend.io). In terms of threat intelligence sources this URL and associated domain are in the blacklist. After deep investigation I found some malicious activities on EmilyComp’s machine. Device has been contained. I will escalate this case to tier-2 for further investigation.
Artifacts:
Request URL: http://mogagrocol.ru/wp-content/plugins/akismet/fv/index.php?email=ellie@letsdefend.io
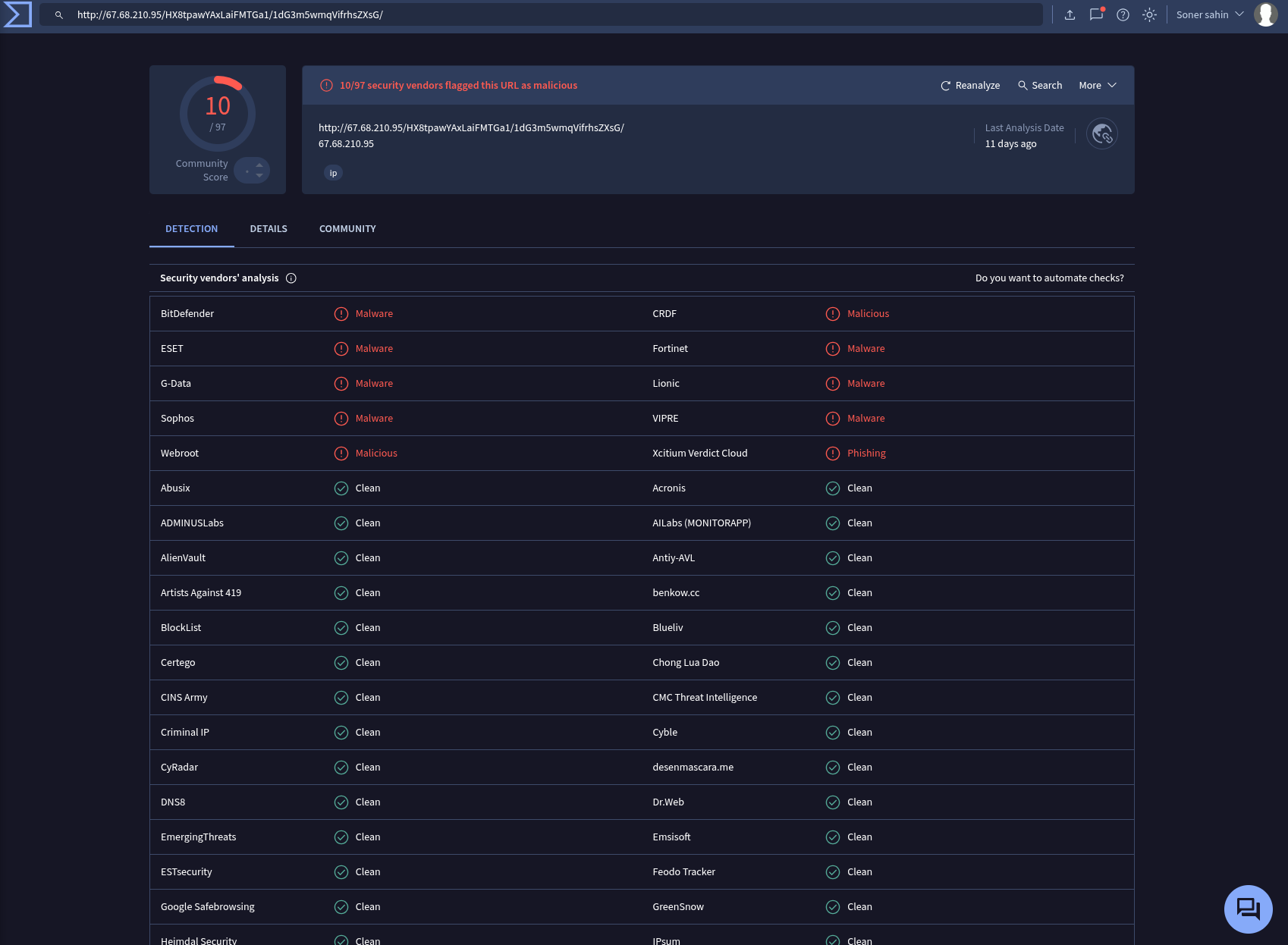
Request URL: http://67.68.210.95/HX8tpawYAxLaiFMTGa1/1dG3m5wmqVifrhsZXsG/
URL: http://162.241.242.173:8080/HQ9TemntfBzghL/3wz57awaSHlQrrnP/S78n2aUqY7U/
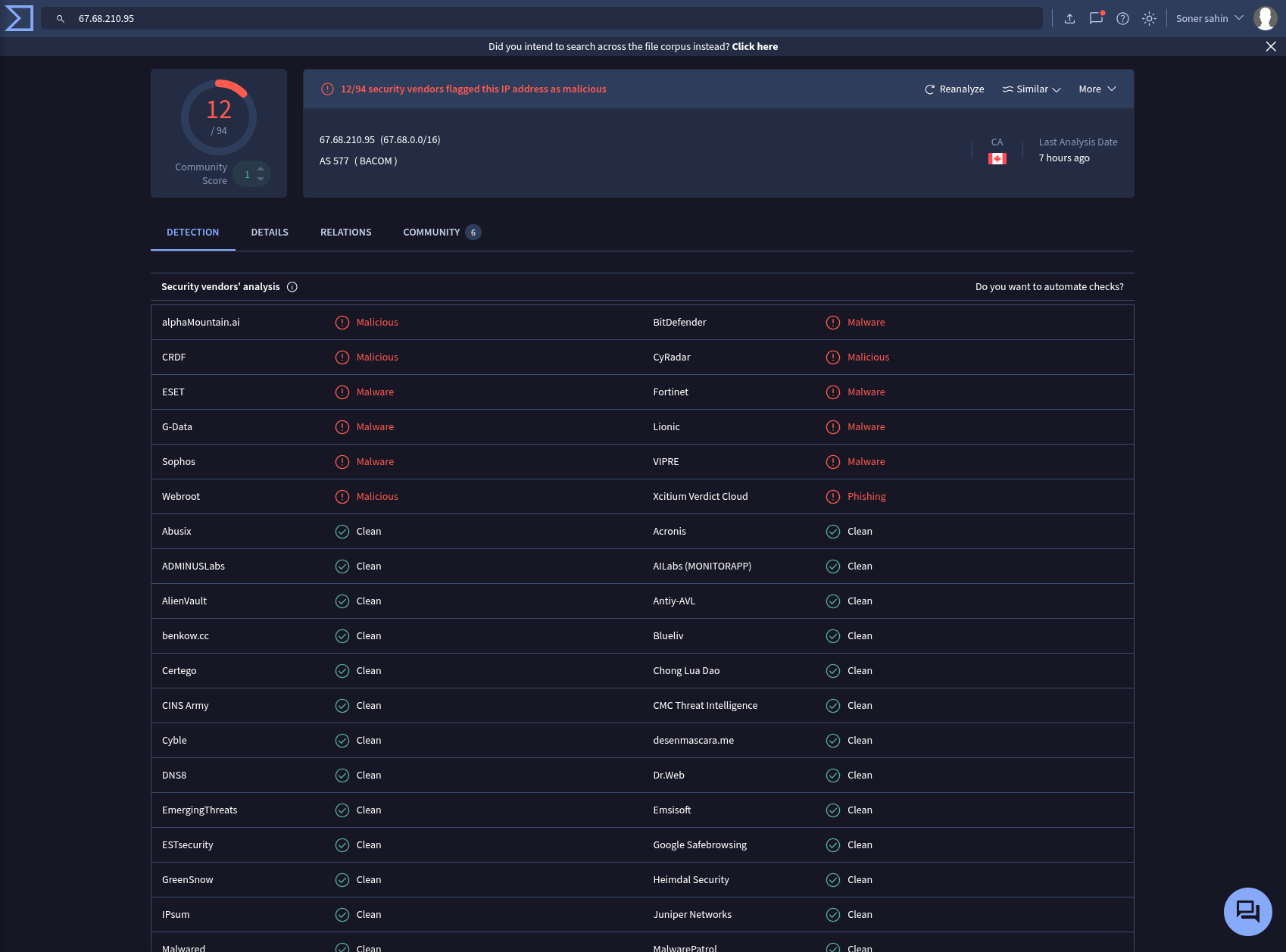
URL: http://67.68.210.95/2SjAcA5VhhJiFjBQ/vvszin6AicmidnG5bg/DaDVVYvfEHlcIIcgcu/0U5UiIkaHankrHGa/FYSJmdQDj2ejni1UI/
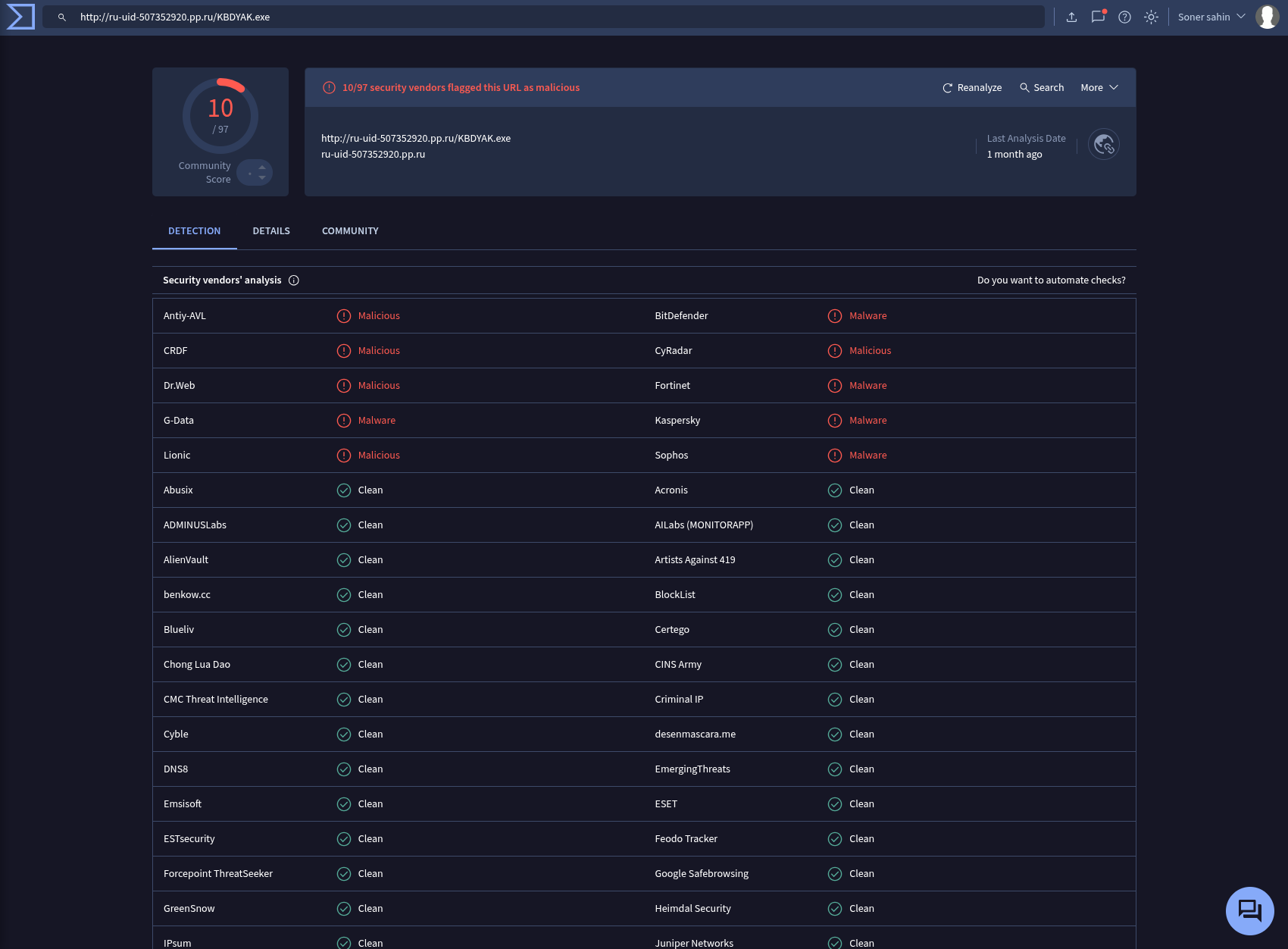
URL: http://ru-uid-507352920.pp.ru/KBDYAK.exe
IP: 162.241.242.173
IP: 67.68.210.95
IP: 91.189.114.8
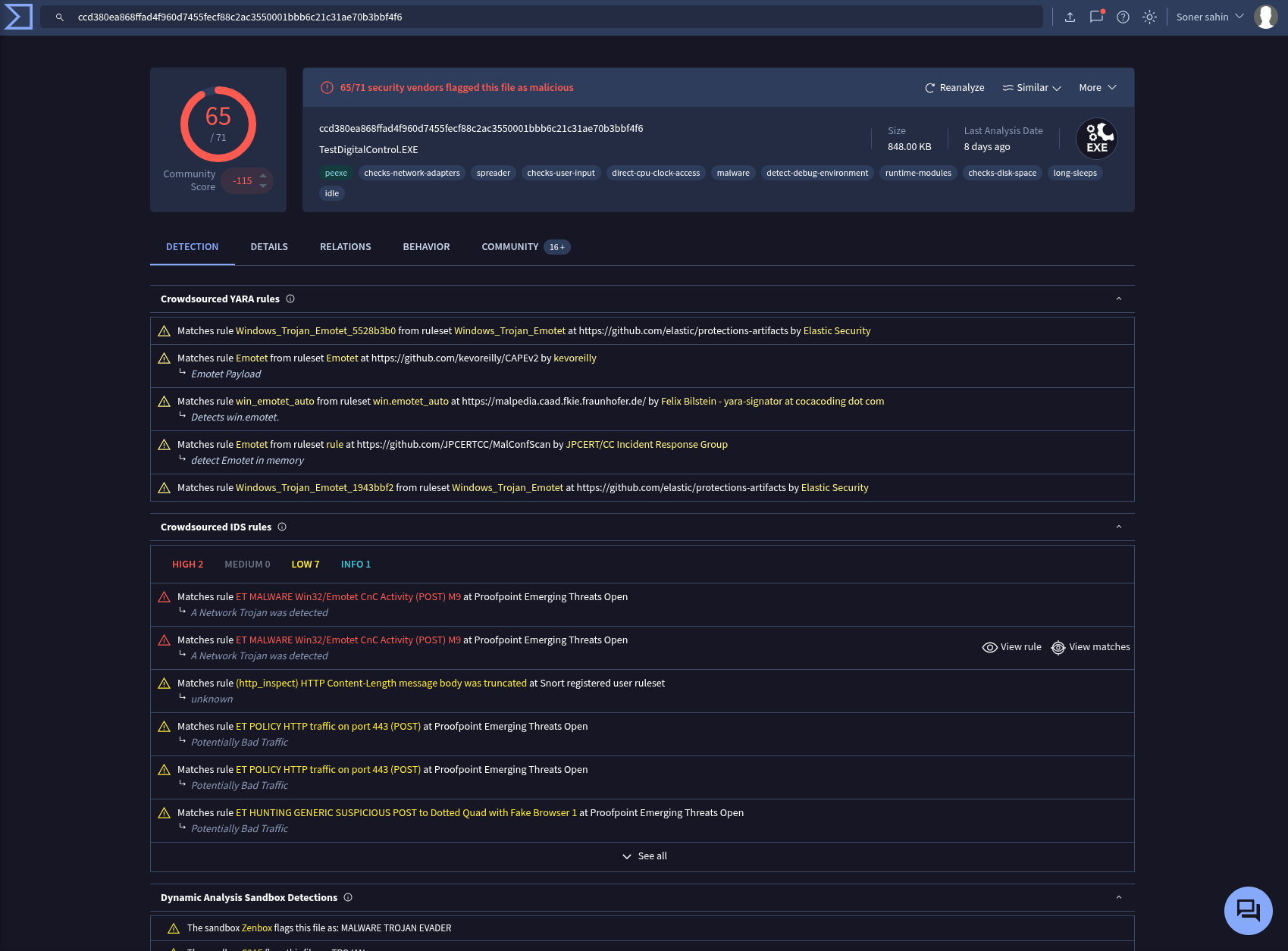
KBDYAK.exe
Hash: ccd380ea868ffad4f960d7455fecf88c2ac3550001bbb6c21c31ae70b3bbf4f6
Thank you for taking the time to read this write-up! I hope you found it insightful and helpful.
Keep learning and stay sharp. 👊
Keep up the good work!