[EN] Wazuh File Integrity Monitoring (FIM)
Hi everyone, in this article I’ll introduce you to Wazuh’s File Integrity Monitoring feature.
FIM is one of Wazuh’s most powerful features that monitors your environments for new files, changes, and more.
With this feature, you have great monitoring, visibility, and awareness capabilities over your environments.
You can also integrate it with YARA, VirusTotal, ClamAV, and CDB Lists to identify whether files are harmful or not. This is a great capability, and I’ll show you how to integrate them in the next ones.
Let’s see how to monitor a path.
This config is deployed on the client machines. You can deploy it via the Wazuh dashboard or by manually adding the configs on each client.
The config file is /var/ossec/etc/ossec.conf
Here is a basic example of the FIM config.
1 <!-- File integrity monitoring -->
2 <syscheck>
3
4 <!-- Default -->
5 <!-- Directories to check (perform all possible verifications) -->
6 <directories>/etc,/usr/bin,/usr/sbin</directories>
7 <directories>/bin,/sbin,/boot</directories>
8
9
10 <!-- Custom-->
11 <!-- In this section you'll add the paths to be monitored for Linux environment -->
12 <directories realtime="yes" report_changes="yes" check_md5sum="yes" check_all="yes">/root</directories>
13 <directories realtime="yes" report_changes="yes" check_md5sum="yes" check_all="yes">/home/ubuntu</directories>
14 <directories realtime="yes" report_changes="yes" check_md5sum="yes" check_all="yes">/etc</directories>
15
16
17 <!-- Custom-->
18 <!-- In this section you'll add the paths to be monitored for Windows environment -->
19 <directories realtime="yes" report_changes="yes" check_md5sum="yes" check_all="yes">C:/Users</directories>
20 <directories realtime="yes" report_changes="yes" check_md5sum="yes" check_all="yes">D:/abc</directories>
21
22
23 <!-- Files/directories to ignore -->
24 <!-- Here you'll add files to be ignored -->
25 <ignore>/etc/mtab</ignore>
26 <ignore>/etc/hosts.deny</ignore>
27
28
29 <!-- File types to ignore -->
30 <!-- Here you'll add file types to be ignored -->
31 <ignore type="sregex">.log$|.swp$</ignore>
32
33 </syscheck>
Restart the service
1sudo systemctl restart wazuh-agent
In this file, you can add the paths to be monitored in Linux, Windows, and macOS environments, ignore files or directories to reduce false positives, and ignore file types.
This is just a basic but useful configuration. Keep in mind that you’ll also be able to schedule scans, add more file attributes to record, add more exclusions, and much more.
Here is what you’re able to do with Wazuh’s FIM feature.
Demo:
I’ve configured FIM on my lab environment and will show you how it looks on the Wazuh dashboard.
I’ll add a file named malware.cc in the /home/ubuntu/Downloads/ folder on one of the client machines.
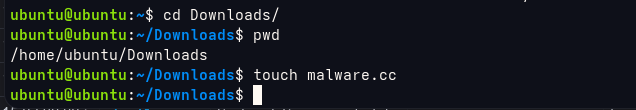
Wazuh Dashboard
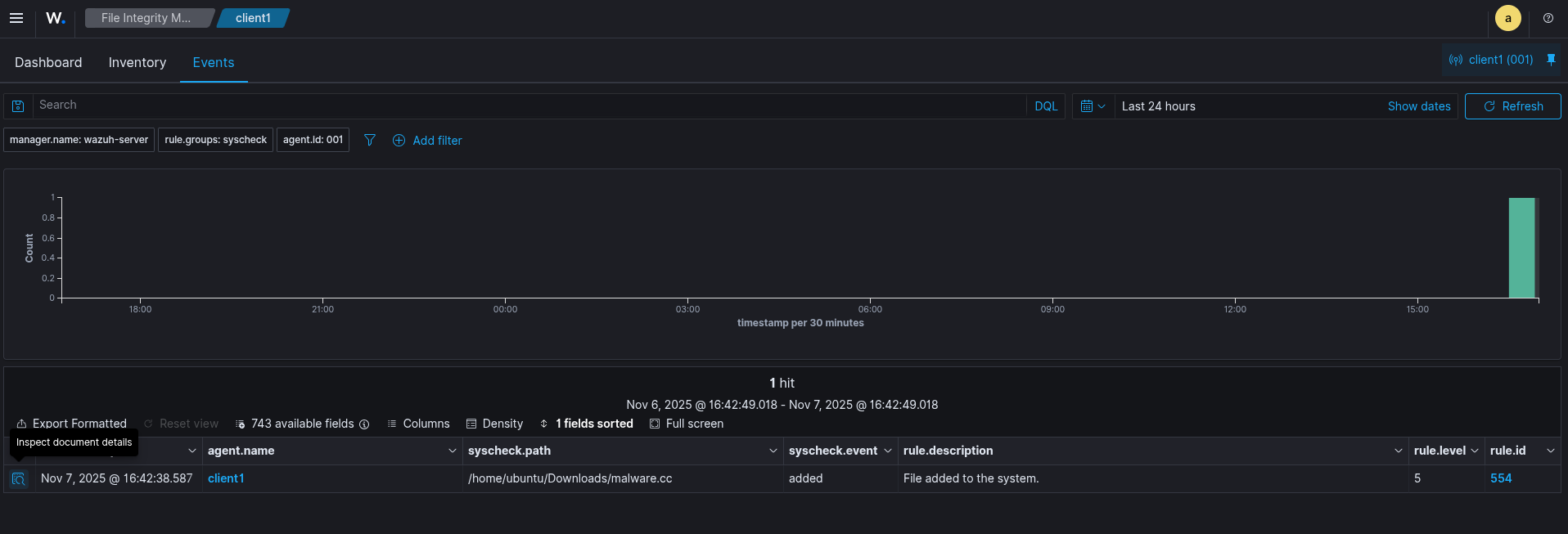
JSON Output
1{
2 "_index": "wazuh-alerts-4.x-2025.11.07",
3 "_id": "QfD7XpoBs8kxnuBm99FE",
4 "_score": null,
5 "_source": {
6 "syscheck": {
7 "uname_after": "ubuntu",
8 "mtime_after": "2025-11-07T15:42:38",
9 "size_after": "0",
10 "gid_after": "1000",
11 "mode": "realtime",
12 "path": "/home/ubuntu/Downloads/malware.cc",
13 "sha1_after": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
14 "gname_after": "ubuntu",
15 "uid_after": "1000",
16 "perm_after": "rw-rw-r--",
17 "event": "added",
18 "md5_after": "d41d8cd98f00b204e9800998ecf8427e",
19 "sha256_after": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
20 "inode_after": 6029902
21 },
22 "input": {
23 "type": "log"
24 },
25 "agent": {
26 "ip": "192.168.1.118",
27 "name": "client1",
28 "id": "001"
29 },
30 "manager": {
31 "name": "wazuh-server"
32 },
33 "rule": {
34 "firedtimes": 1,
35 "mail": false,
36 "level": 5,
37 "pci_dss": [
38 "11.5"
39 ],
40 "hipaa": [
41 "164.312.c.1",
42 "164.312.c.2"
43 ],
44 "tsc": [
45 "PI1.4",
46 "PI1.5",
47 "CC6.1",
48 "CC6.8",
49 "CC7.2",
50 "CC7.3"
51 ],
52 "description": "File added to the system.",
53 "groups": [
54 "ossec",
55 "syscheck",
56 "syscheck_entry_added",
57 "syscheck_file"
58 ],
59 "id": "554",
60 "nist_800_53": [
61 "SI.7"
62 ],
63 "gpg13": [
64 "4.11"
65 ],
66 "gdpr": [
67 "II_5.1.f"
68 ]
69 },
70 "location": "syscheck",
71 "decoder": {
72 "name": "syscheck_new_entry"
73 },
74 "id": "1762530158.1059299",
75 "full_log": "File '/home/ubuntu/Downloads/malware.cc' added\nMode: realtime\n",
76 "timestamp": "2025-11-07T15:42:38.587+0000"
77 },
78 "fields": {
79 "syscheck.mtime_after": [
80 "2025-11-07T15:42:38.000Z"
81 ],
82 "timestamp": [
83 "2025-11-07T15:42:38.587Z"
84 ]
85 },
86 "sort": [
87 1762530158587
88 ]
89}
Now, let me add something inside that file.
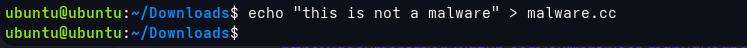
Wazuh Dashboard
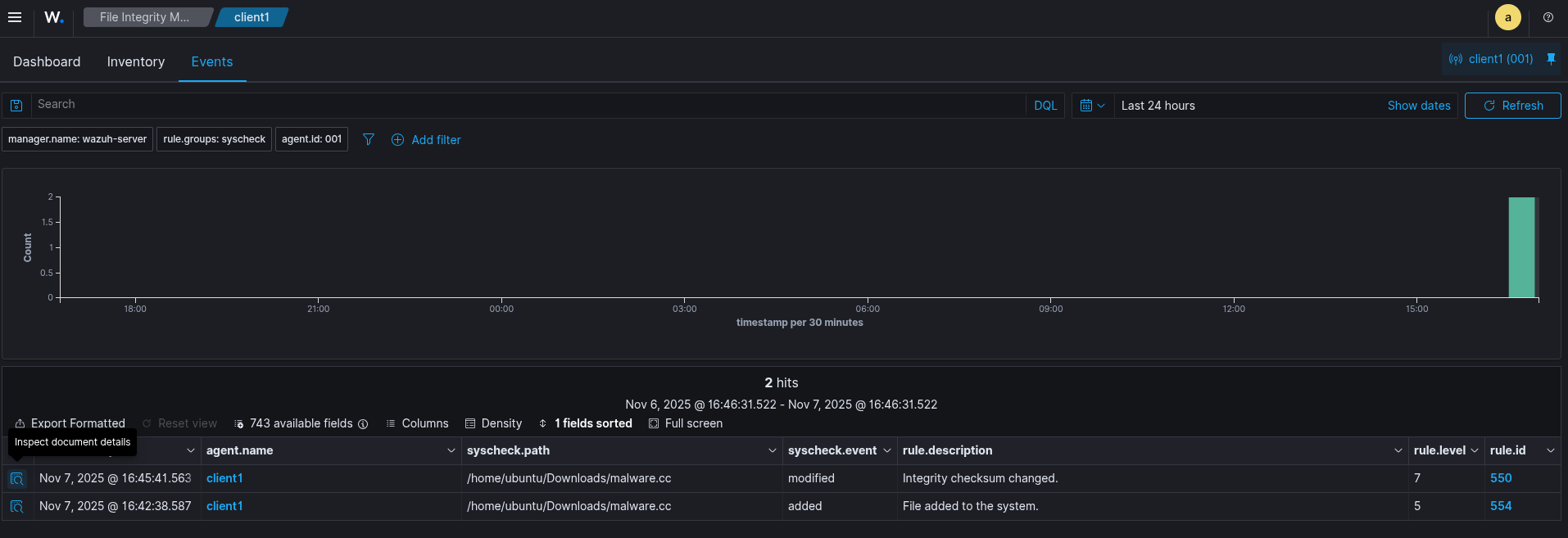
JSON Output
1{
2 "_index": "wazuh-alerts-4.x-2025.11.07",
3 "_id": "T_D-XpoBs8kxnuBmutG-",
4 "_score": null,
5 "_source": {
6 "syscheck": {
7 "size_before": "0",
8 "uname_after": "ubuntu",
9 "mtime_after": "2025-11-07T15:45:41",
10 "size_after": "22",
11 "gid_after": "1000",
12 "md5_before": "d41d8cd98f00b204e9800998ecf8427e",
13 "diff": "0a1\n> this is not a malware\n",
14 "sha256_before": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
15 "mtime_before": "2025-11-07T15:42:38",
16 "mode": "realtime",
17 "path": "/home/ubuntu/Downloads/malware.cc",
18 "sha1_after": "0305ee037a2380eaa71c6cf2e07778032fdbcef2",
19 "changed_attributes": [
20 "size",
21 "mtime",
22 "md5",
23 "sha1",
24 "sha256"
25 ],
26 "gname_after": "ubuntu",
27 "uid_after": "1000",
28 "perm_after": "rw-rw-r--",
29 "event": "modified",
30 "md5_after": "c830a5a786c739b8b39edfb82310b009",
31 "sha1_before": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
32 "sha256_after": "80d6e49563d0ed0c735868ac7f9cb428ea95137b067e39dfd1dfb60974c779be",
33 "inode_after": 6029902
34 },
35 "input": {
36 "type": "log"
37 },
38 "agent": {
39 "ip": "192.168.1.118",
40 "name": "client1",
41 "id": "001"
42 },
43 "manager": {
44 "name": "wazuh-server"
45 },
46 "rule": {
47 "mail": false,
48 "level": 7,
49 "pci_dss": [
50 "11.5"
51 ],
52 "hipaa": [
53 "164.312.c.1",
54 "164.312.c.2"
55 ],
56 "tsc": [
57 "PI1.4",
58 "PI1.5",
59 "CC6.1",
60 "CC6.8",
61 "CC7.2",
62 "CC7.3"
63 ],
64 "description": "Integrity checksum changed.",
65 "groups": [
66 "ossec",
67 "syscheck",
68 "syscheck_entry_modified",
69 "syscheck_file"
70 ],
71 "nist_800_53": [
72 "SI.7"
73 ],
74 "gdpr": [
75 "II_5.1.f"
76 ],
77 "firedtimes": 1,
78 "mitre": {
79 "technique": [
80 "Stored Data Manipulation"
81 ],
82 "id": [
83 "T1565.001"
84 ],
85 "tactic": [
86 "Impact"
87 ]
88 },
89 "id": "550",
90 "gpg13": [
91 "4.11"
92 ]
93 },
94 "location": "syscheck",
95 "decoder": {
96 "name": "syscheck_integrity_changed"
97 },
98 "id": "1762530341.1063077",
99 "full_log": "File '/home/ubuntu/Downloads/malware.cc' modified\nMode: realtime\nChanged attributes: size,mtime,md5,sha1,sha256\nSize changed from '0' to '22'\nOld modification time was: '1762530158', now it is '1762530341'\nOld md5sum was: 'd41d8cd98f00b204e9800998ecf8427e'\nNew md5sum is : 'c830a5a786c739b8b39edfb82310b009'\nOld sha1sum was: 'da39a3ee5e6b4b0d3255bfef95601890afd80709'\nNew sha1sum is : '0305ee037a2380eaa71c6cf2e07778032fdbcef2'\nOld sha256sum was: 'e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855'\nNew sha256sum is : '80d6e49563d0ed0c735868ac7f9cb428ea95137b067e39dfd1dfb60974c779be'\n",
100 "timestamp": "2025-11-07T15:45:41.563+0000"
101 },
102 "fields": {
103 "syscheck.mtime_after": [
104 "2025-11-07T15:45:41.000Z"
105 ],
106 "syscheck.mtime_before": [
107 "2025-11-07T15:42:38.000Z"
108 ],
109 "timestamp": [
110 "2025-11-07T15:45:41.563Z"
111 ]
112 },
113 "sort": [
114 1762530341563
115 ]
116}
That’s how it looks.
As I mentioned, FIM is much more than this. Depending on your needs, environments, etc., you’re able to configure it accordingly.
Thanks for reading, I hope you’ll find it useful.
Keep up the good work!