[EN] Wazuh Auditd Integration
Hi everyone! In this article I’ll walk you through installing Auditd on a Linux system and integrating it with Wazuh.
Auditd (the Linux Auditing System) records security-relevant activity so you can understand what is happening on your hosts. By tailoring the ruleset, you can increase visibility and build detections that match your environment.
Installation
Install Auditd on Debian/Ubuntu with the following command:
1sudo apt -y install auditd
Start the service and enable it at boot:
1sudo systemctl start auditd
2sudo systemctl enable auditd
Add the rules to the /etc/audit/audit.rules file.
1echo "-a exit,always -F auid=1000 -F egid!=994 -F auid!=-1 -F arch=b32 -S execve -k audit-wazuh-c" >> /etc/audit/audit.rules
2echo "-a exit,always -F auid=1000 -F egid!=994 -F auid!=-1 -F arch=b64 -S execve -k audit-wazuh-c" >> /etc/audit/audit.rules
If you need more comprehensive coverage, consider importing community-maintained rule sets such as:
- Neo23x0/auditd
- prathamghadge/audit.rules
- bfuzzy/auditd-attack
- linux-audit/audit-userspace/rules
- znsstudio/audit.rules
- coh7eiqu8thaBu/audit.rules
Reload the rules and confirm they are active:
1sudo auditctl -R /etc/audit/audit.rules
2sudo auditctl -l
Example output:
1No rules
2enabled 1
3failure 1
4pid 267349
5rate_limit 0
6backlog_limit 8192
7lost 0
8backlog 3
9backlog_wait_time 60000
10backlog_wait_time_actual 0
11enabled 1
12failure 1
13pid 267349
14rate_limit 0
15backlog_limit 8192
16lost 0
17backlog 7
18backlog_wait_time 60000
19backlog_wait_time_actual 0
20enabled 1
21failure 1
22pid 267349
23rate_limit 0
24backlog_limit 8192
25lost 0
26backlog 9
27backlog_wait_time 60000
28backlog_wait_time_actual 0
29-a always,exit -F arch=b32 -S execve -F auid=1000 -F egid!=994 -F auid!=-1 -F key=audit-wazuh-c
30-a always,exit -F arch=b64 -S execve -F auid=1000 -F egid!=994 -F auid!=-1 -F key=audit-wazuh-c
Auditd configuration files live in /etc/audit, and logs are written to /var/log/audit/audit.log.
Wazuh Integration
The next step is to forward Auditd logs to Wazuh. The instructions below assume you already have the Wazuh manager and agent installed.
Wazuh agent:
1sudo nano /var/ossec/etc/ossec.conf
Add the following block near the end of the configuration file to ingest Auditd logs:
1<localfile>
2 <log_format>audit</log_format>
3 <location>/var/log/audit/audit.log</location>
4</localfile>
Restart the agent to apply the change:
1sudo systemctl restart wazuh-agent
Wazuh manager:
Verify that the Auditd key list contains the expected values:
1cat /var/ossec/etc/lists/audit-keys
2
3audit-wazuh-w:write
4audit-wazuh-r:read
5audit-wazuh-a:attribute
6audit-wazuh-x:execute
7audit-wazuh-c:command
Catch everything!
To raise high-priority alerts for suspicious commands, create (or edit) a lookup list that tags binaries as suspicious:
1sudo nano /var/ossec/etc/lists/suspicious-programs
1tcpdump:suspicious
2whoami:suspicious
3uname:suspicious
4wget:suspicious
5rm:suspicious
6grep:suspicious
Reference the list under the <ruleset> section in ossec.conf:
1sudo nano /var/ossec/etc/ossec.conf
2
3<list>etc/lists/suspicious-programs</list>
Create a custom rule that raises an alert whenever one of these commands runs:
1sudo nano /var/ossec/etc/rules/local_rules.xml
2
3<group name="audit">
4 <rule id="100210" level="12">
5 <if_sid>80792</if_sid>
6 <list field="audit.command" lookup="match_key_value" check_value="suspicious">etc/lists/suspicious-programs</list>
7 <description>Audit: Highly Suspicious Command executed: $(audit.exe)</description>
8 <group>audit_command,</group>
9 </rule>
10</group>
Restart the Wazuh manager so the new rule takes effect:
1sudo systemctl restart wazuh-manager
Attack emulation
Trigger a few of the suspicious commands on a monitored endpoint to generate events:
1root@ubuntu:/home/ubuntu# grep
2Usage: grep [OPTION]... PATTERNS [FILE]...
3Try 'grep --help' for more information.
4
5root@ubuntu:/home/ubuntu# uname
6Linux
7
8root@ubuntu:/home/ubuntu# whoami
9root
Wazuh
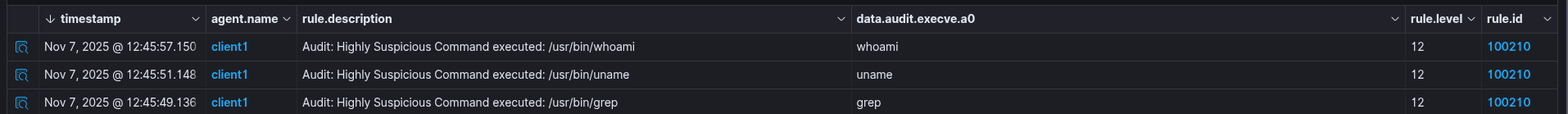
JSON output
1{
2 "_index": "wazuh-alerts-4.x-2025.11.07",
3 "_id": "RvAjXpoBs8kxnuBmRsyH",
4 "_score": null,
5 "_source": {
6 "input": {
7 "type": "log"
8 },
9 "agent": {
10 "ip": "192.168.1.118",
11 "name": "client1",
12 "id": "001"
13 },
14 "manager": {
15 "name": "wazuh-server"
16 },
17 "data": {
18 "audit": {
19 "syscall": "59",
20 "gid": "0",
21 "fsgid": "0",
22 "session": "5",
23 "pid": "7443",
24 "suid": "0",
25 "type": "SYSCALL",
26 "uid": "0",
27 "egid": "0",
28 "exe": "/usr/bin/whoami",
29 "file": {
30 "inode": "2363254",
31 "mode": "0100755",
32 "name": "/usr/bin/whoami"
33 },
34 "sgid": "0",
35 "id": "1373",
36 "key": "audit-wazuh-c",
37 "auid": "1000",
38 "execve": {
39 "argc": "1",
40 "a0": "whoami"
41 },
42 "euid": "0",
43 "command": "whoami",
44 "ppid": "4881",
45 "fsuid": "0",
46 "exit": "0",
47 "cwd": "/home/ubuntu",
48 "success": "yes",
49 "tty": "pts2",
50 "arch": "c000003e"
51 }
52 },
53 "rule": {
54 "firedtimes": 3,
55 "mail": true,
56 "level": 12,
57 "description": "Audit: Highly Suspicious Command executed: /usr/bin/whoami",
58 "groups": [
59 "auditaudit_command"
60 ],
61 "id": "100210"
62 },
63 "location": "/var/log/audit/audit.log",
64 "decoder": {
65 "parent": "auditd",
66 "name": "auditd"
67 },
68 "id": "1762515957.74820",
69 "full_log": "type=SYSCALL msg=audit(1762515956.917:1373): arch=c000003e syscall=59 success=yes exit=0 a0=5802fab5e320 a1=5802fab5e2c0 a2=5802fab24d50 a3=5802fab5e2c0 items=2 ppid=4881 pid=7443 auid=1000 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts2 ses=5 comm=\"whoami\" exe=\"/usr/bin/whoami\" subj=unconfined key=\"audit-wazuh-c\"\u001dARCH=x86_64 SYSCALL=execve AUID=\"ubuntu\" UID=\"root\" GID=\"root\" EUID=\"root\" SUID=\"root\" FSUID=\"root\" EGID=\"root\" SGID=\"root\" FSGID=\"root\" type=EXECVE msg=audit(1762515956.917:1373): argc=1 a0=\"whoami\" type=CWD msg=audit(1762515956.917:1373): cwd=\"/home/ubuntu\" type=PATH msg=audit(1762515956.917:1373): item=0 name=\"/usr/bin/whoami\" inode=2363254 dev=fc:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 nametype=NORMAL cap_fp=0 cap_fi=0 cap_fe=0 cap_fver=0 cap_frootid=0\u001dOUID=\"root\" OGID=\"root\" type=PATH msg=audit(1762515956.917:1373): item=1 name=\"/lib64/ld-linux-x86-64.so.2\" inode=2394929 dev=fc:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 nametype=NORMAL cap_fp=0 cap_fi=0 cap_fe=0 cap_fver=0 cap_frootid=0\u001dOUID=\"root\" OGID=\"root\" type=PROCTITLE msg=audit(1762515956.917:1373): proctitle=\"whoami\"",
70 "timestamp": "2025-11-07T11:45:57.150+0000"
71 },
72 "fields": {
73 "timestamp": [
74 "2025-11-07T11:45:57.150Z"
75 ]
76 },
77 "sort": [
78 1762515957150
79 ]
80}
That’s it! Feel free to extend these examples to match your environment so you can improve visibility, efficiency, and security.
Thank you for taking time to read this article, I hope you’ll find this article useful.
Keep up the good work!